ZLAB MALWARE ANALYSIS REPORT: RANSOMWARE-AS-A-SERVICE PLATFORMS
Introduction
Over the years, the diffusion of darknets has created new illegal business models. Along with classic illegal goods such as drugs and payment card data, other services appeared in the criminal underground, including hacking services and malware development. New platforms allow crooks without technical skills to create their own ransomware and spread it.
Ransomware is malicious code that infects the victims' machines and blocks or encrypts their files, requesting a ransom payment. When ransomware is installed on a victim's machine, it searches for and targets sensitive files and data, including financial data, databases and personal files. Ransomware is developed to make the victim's machine unusable. The user has only two options: pay the ransom without having the guarantee of getting back the original files or format the PC by disconnecting it from the Internet.
Hands-on threat intel training
Ransomware history
The first ransomware was born in 1989 when 20,000 floppy disks were dispatched as "AIDS Information-introductory Diskettes." After 90 reboots, the software hid directories and encrypted the names of files on the customer's computer, claiming a ransom of $189. The payment had to be made by depositing the requested amount at a post office box in Panama.
After many years, in May 2005, GpCode, TROJ.RANSOM.A, Archiveus, Krotten, and others appeared and in the threat landscape-
With the advent of the new anonymous payment method, such as Bitcoin, at the end of 2008, ransomware has adopted new payment methods.
Many ransomware families, such as CryptoLocker, TeslaCrypt, and Locky, compromised an impressive number of systems worldwide, but the WannaCry Ransomware Attack is currently considered the most devastating of all cyber-attacks.
In a few hours after discovery, the malware was able to infect more than 230k machines exploiting a vulnerability in the SMB protocol. Despite its unexpected worm-like behavior, WannaCry continued to encrypt the user files using the classic methods but asked for a payment of $300.
The samples related to the last ten years' attacks could be grouped into two different categories:
- Locker-ransomware: is ransomware that locks users out of their devices
- Crypto-ransomware: is ransomware that encrypts files, directories, and hard drives
The first type was used between 2008 and 2011. It was discarded because it was quite simple to eliminate the infection without paying the ransom. In fact, locker-ransomware has a weakness. It shows a window that denies access to the computer, but the ransomware lock was easy to bypass.
The second type does not have this problem because crypto-malware directly hits the users' files and denies the victim usage of the system. Obviously, the user cannot access the information contained in the encrypted files.
Then the next ransomware uses the same encrypting approach as the second one, but they involve a combination of advanced distribution efforts and development techniques used to ensure evasion and anti-analysis, as Locky and WannaCry attest.
Obviously, the creation of ransomware needs specific and advanced skills, but the great interest of the criminal organization in the extortion model implemented by this kind of malware pushed the creation of new services that allows crooks to create their ransomware without having specific knowledge. Welcome to the Ransomware-as-a-Service (RaaS) business model.
Ransomware-as-a-Service
The rise of the RaaS business model is giving wannabe criminals an effortless way to launch a cyber-extortion campaign without having technical expertise, and it is the cause of flooding the market with new ransomware strains.
Ransomware-as-a-Service is a profitable model for both malware sellers and their customers. Using this approach, malware sellers can acquire new infection vectors and potentially reach new victims they cannot reach through a conventional approach, such as email spamming or compromised websites. RaaS customers can easily obtain ransomware via RaaS portals by configuring a few features and distributing the malware to unwitting victims.
RaaS platforms cannot be found on the Clearnet, so they are hidden on the dark side of the Internet, the Dark Web.
Surfing the dark web through unconventional search engines, you can find several websites that offer RaaS. Each one provides different features for their ransomware, allowing users to select the file extensions considered by the encrypting phase, the ransom demanded by the victim and other technical functionality that the malware will implement.
Furthermore, beyond the usage of RaaS platforms, custom malicious software can be purchased through crime forums or websites where one can hire a hacker to create one's personal malware. Historically, this commerce has always existed, but it was specialized in cyber-attacks, such as espionage, hacking of accounts and website defacement. Only when hackers understood it could be profitable they started to provide this specific service.
The supply of this type of service is offered substantially in two ways: hiring someone to write malware with the requirements defined by the customer or using a Ransomware-as-a-Service platform.
RaaSberry
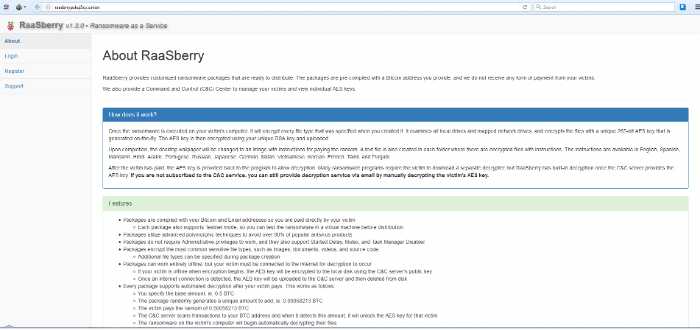
RaaSberry provides customized ransomware packages that are ready to be distributed. The packages are pre-compiled with a Bitcoin address provided by the customers, and the platform creators do not receive any form of payment from your victims.
Once the ransomware is executed on your victim's computer, it will encrypt every file type specified when you created it. It examines all local and mapped network drives and encrypts the files with a unique 265-bit AES key that is generated on the fly. The AES key is then encrypted using your unique RSA key and uploaded.
Upon completion, the desktop wallpaper will be changed to an image with instructions for paying the ransom. A text file is also created in each folder, with encrypted files with instructions. The instructions are available in English, Spanish, Mandarin, Hindi, Arabic, Portuguese, Russian, Japanese, German, Italian, Vietnamese, Korean, French, Tamil, and Punjabi.
After the victim has paid, the AES key is returned to the program to allow decryption. Many ransomware programs require the victim to download a separate decryptor, but RaaSberry has built-in decryption once the COMMAND AND CONTROL server provides the AES key. If you are not subscribed to the COMMAND AND CONTROL service, you can still provide a decryption service via email by manually decrypting the victim's AES key. This website has several sections: About, Login, Register and Support. The About section describes how you can create your personal ransomware.
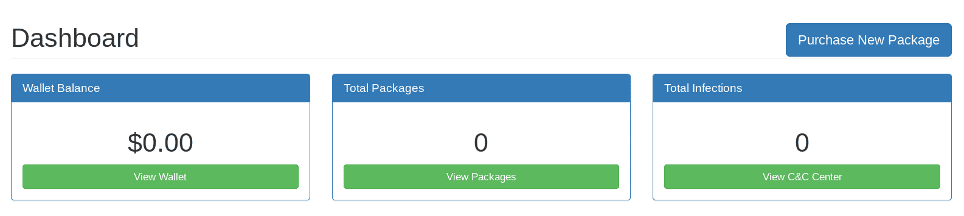
A set of statistics about the ransomware campaign, keeping track of the number of infections, the number of paying people and the relative monetary earnings are available in the user's personal section.
In this dashboard, you can purchase new packages that include, for each plan, the same ransomware but a different subscription length to Command and Control. As shown in the following figure, there are several plans:
- Plastic: One-month COMMAND AND CONTROL subscription - $60
- Bronze: Three-month COMMAND AND CONTROL subscription - $150
- Silver: Six-month COMMAND AND CONTROL subscription - $250
- Gold: One-year COMMAND AND CONTROL subscription - $400
- Platinum: Three years COMMAND AND CONTROL subscription - $650
Once the users register to the platform and purchase a new package, the platform assigns them a personal bitcoin address. They can control statistics about the ransomware campaign and check their earnings.
Furthermore, you can ask for assistance from the creator of this platform by sending an ad hoc email.
Ranion
Another platform that offers a similar service is Ranion. The novelty is that the Ranion team declares that the COMMAND AND CONTROL of their "Fully UnDetectable" ransomware are established in the Darknet. This site is continuously updated by its operators.
The Ranion team's website shows an example of the COMMAND AND CONTROL dashboard. In the next figure, we can observe the subscription time and when it expires, as well as the infected machines classified by Computer ID, the username of the victim, operation system, IP Address, date of infection, number of encrypted files and the relative encryption key.
In this dashboard, users can purchase new packages that include, for each plan, the same ransomware but a different subscription time to the Command and Control. As shown in the next figure, there are two plans in which the ransomware is the same, but there is a different subscription time to the COMMAND AND CONTROL dashboard, with different prices.
The next figure shows the explicit Bitcoin address, who sends the package's price, and the email to contact with the further information required:
- Chosen package
- Your bitcoin address used to send money
- Your own Bitcoin address to receive money from your Clients
- Your price to receive from your Clients
- Your email address to get contacted by your Clients
- If you want to keep track of the IPs of your Clients ( enabled by default )
- Optional additions
The Ransomware Decrypter is shown in the next figure. This is used by the victims to decrypt files with the key sent by the criminals once they have paid the ransom. Pressing the "decrypt my files" button, the decryption process of files starts.
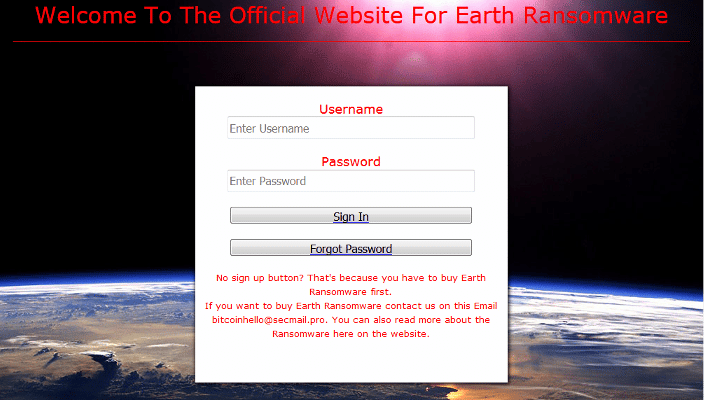
EarthRansomware
Another RaaS platform is earthRansomware. The following image shows the home page of the site. Customers can log in to the platform after buying their personal ransomware by contacting the EarthRansomware team by email.
The website included a session that provided a step-by-step tutorial for services.
Unlike the previous RaaS, this one offers a fixed-rate service at 0.3 BTC. When the customer pays the quote to the bitcoin address indicated in the mail, he obtains his credentials to enter the personal section.
In this area of the site, users can customize their ransomware settings:
- Amount of bitcoins you require
- Your email address
- First payment deadline – Last payment deadline
- Bitcoin address
Once a system is infected, the malware will show the ransom note notifying victims of the deadline for the payment and instructions to pay the ransom.
Redfox ransomware
Redfox is a unique Ransom-as-a-service platform because, differently from the others, it is hosted on Clearnet. This ransomware, according to the description provided by the developing team, is the most advanced and customizable malware. RedFox encrypts all user files and shared drives using the BlowFish algorithm.
The webpage says that the Command and Control, hosted in the Tor network, allows users to choose the ransom amount, the payment mode, the payment deadline, personalize the ransom note and other technical features. The RaaS allows its customers to choose the usage of binders, packers, and crypters to guarantee anti-analysis of the sample.
The website does not contain examples or tutorials about command and control usage. However, users can pay and download all the stuff needed to build the criminal infrastructure.
Createyourownransomware
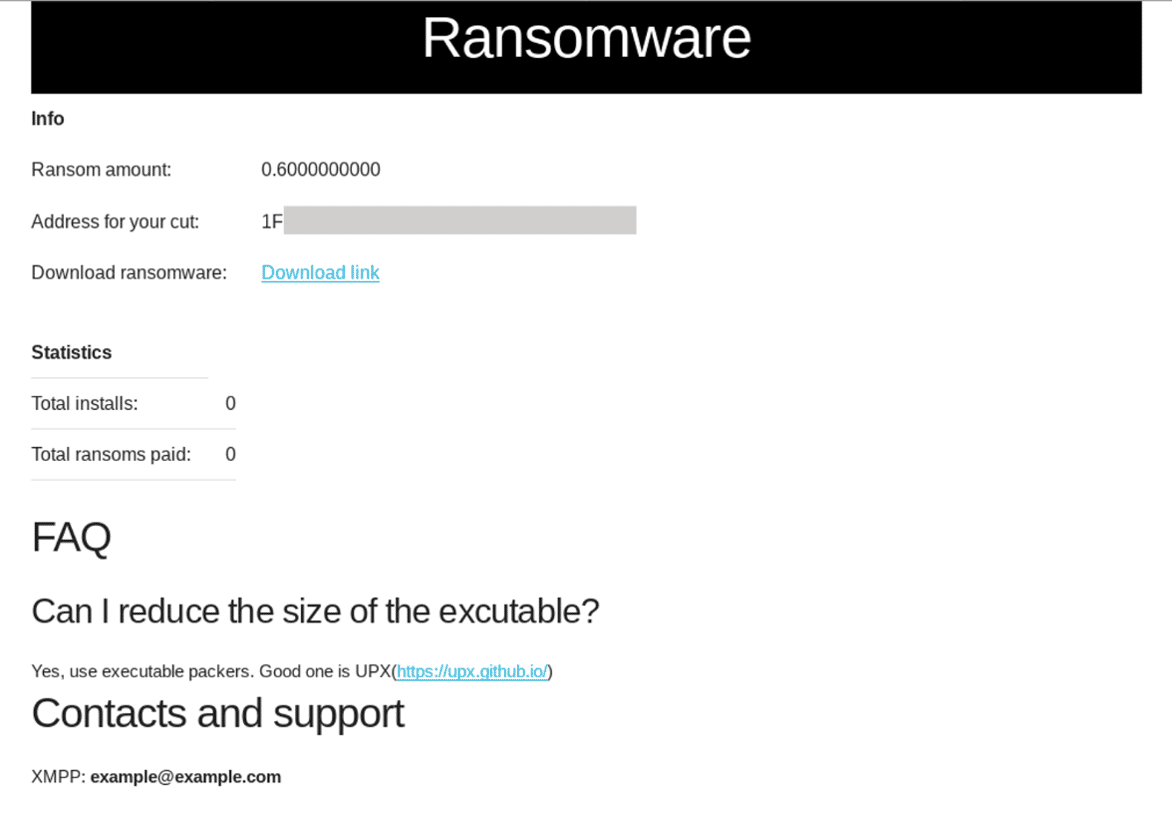
A totally-free platform found in the darknet is Createyourownransomware; its website allows users to download ready-to-go ransomware by filling only the boxes in a form:
- the Bitcoin address to which you want to receive your "money cut."
- the ransom amount
- a simple captcha.
The "money cut" corresponds to 90% of the ransom amount; the remaining amount is the fee that RaaS administrators keep for them to provide the service.
Once the users have filled out the form, the platform will instantly build a new sample and show the link to download the malware. Furthermore, a second webpage shows some statistics about the ransomware campaign, such as the number of infected machines and the number of the paid ransoms.
The user interface of the RaaS, unlike the previous platforms, is very minimal and provides only a few features.
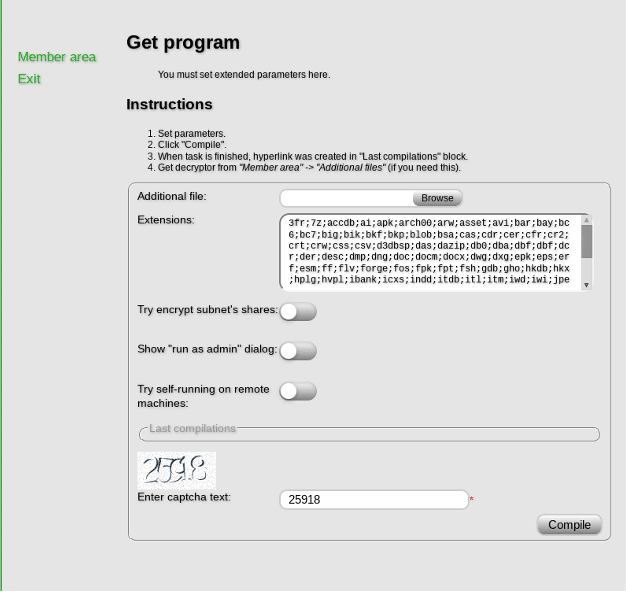
Datakeeper
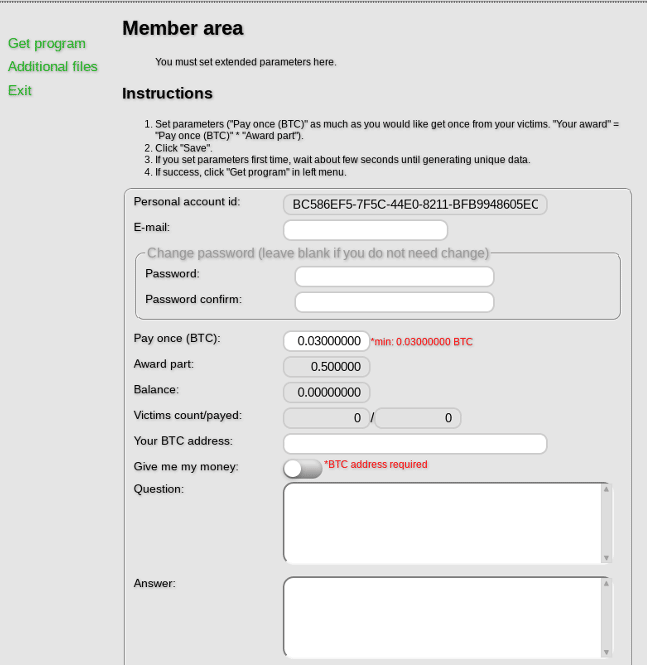
Datakeeper, along with GandCrab and Saturn, is one of the most recent RaaS platforms in the threat landscape. The ransomware created through these platforms infected many machines at the beginning of 2018, demonstrating the increasing interest in using Ransomware-as-a-Service platforms. Currently, only the Datakeeper service is not blocked by law enforcement.
Users can configure their ransomware when registering at the website by choosing a set of features. This platform seems to be one of the more complete because it allows specifying which extension of the files to encrypt.
The Datakeeper team holds 0.5 bitcoin as a service fee for each infection.
In the "Additional files" section, users can download the utility to decrypt the ciphered files.
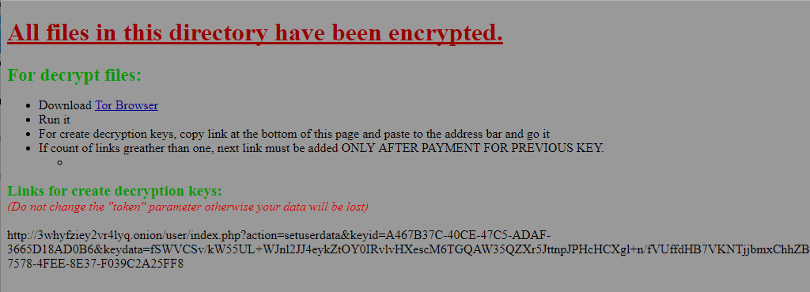
The following figure shows an example ransom note dropped on the victim's machine.
About the Authors:
Pierluigi Paganini
Antonio Pirozzi, Principal Malware Scientist and Senior Threat Researcher at CSE CybSec
Luigi Martire, Malware Researcher at CSE CybSec
Antonio Farina, Malware Researcher at CSE CybSec