Android vulnerability allows attackers to spoof any phone number
Introduction
Because many employees use mobile devices for work, the widespread use of mobile devices has come to put company networks at risk for cyberattacks. Every day, organizations and people in general are targeted by crooks looking for sensitive data they can use to steal identities, sensitive information and commit fraud.
In this article, we analyze a new trick that can be used to display an SMS as coming from any contact on a victim’s phone for performing a successful spoofing attack.
Attacks based on social engineering techniques have been on the rise since a Bitcoin scam took over the social media platform Twitter in July 2020. Twitter revealed that the technique used by crooks is called “phone spearphishing”: it allows attackers to target anyone with an account, including CEOs, celebrities and politicians. Criminals successfully got control of 45 of those accounts and used them to send tweets promoting a bitcoin scam. Through this attack, the attackers successfully manipulated a small number of employees and used their credentials to access Twitter’s internal systems, including getting through our two-factor security mechanisms.
Learn Vulnerability Management
Spoofing an SMS on Android mobile device
As revealed in this article by James Fisher, an attacker can trick Android into displaying an SMS as coming from any contact on a victim’s phone.
“Say I work at Twitter. I have Jack Dorsey, Twitter CEO, saved to my phone’s contacts. I have a previous legit conversation with Jack. Right now, you can send me a message from Jack, which will appear in that conversation history, like this:”
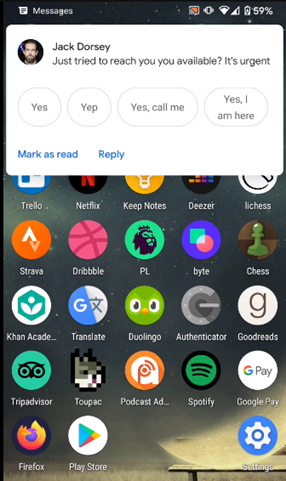
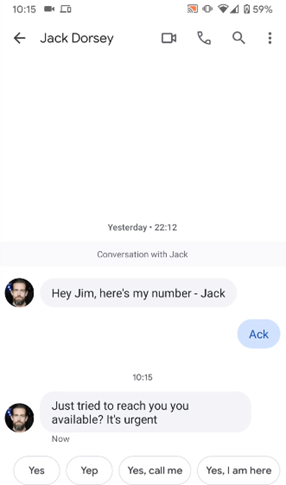
Figure 1: Message impersonation — Android
With this technique in place, attackers can send malicious messages that impersonate any user. As observed above, malicious messages that are completely indistinguishable from genuine messages.
This flaw takes advantage of how Android treats the “Sender ID” of an SMS message. An SMS message on Android can be defined as an alphanumeric “Sender ID” instead of a common number composed of digits.
In this way, imagine that we have an SMS from the Sender ID Twitter, containing a password reset code. As these IDs are not regulated, anyone could send spoof messages using the same Sender ID from Twitter or an arbitrary Sender ID.
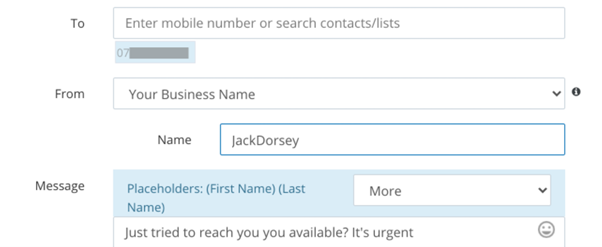
Figure 2 below presents a first scenario where a phishing message that impersonates “JackDorsey” is sent.
Figure 2: Phishing message scenario
Nonetheless, this is a poor phishing scenario, as a new message will appear in a new conversation; the sender would probably not show up as a contact and the message details would show that it is not from a real phone number. This detail could generate a phishing alert.
How to improve the spoofing scenario
The secret to bypass the restriction above is simple: use the Sender ID: 07890123456 — Jack’s number. Taking advantage of the SENDER ID that can be defined as an alphanumeric string, we can replace the digit 0 with the letter O — it’s a valid Sender ID.
As presented in Figure 3 below, the message arrived from the genuine Jack Dorsey contact and is indistinguishable from the genuine message. During the chain, any workflow replaces the letter O with a 0 (zero) and interprets the final string as a real number.
Figure 3: Spoofing attack with the target message
This vulnerability was reported to Google, but it has not yet been mitigated. Thus, criminals can exploit this vector in the wild and impact a large group of users, including high-value targets like CEOs, celebrities and politicians.
Learn Vulnerability Management
Final thoughts
This vulnerability is very dangerous as a criminal can exploit it to spoof any person with an Android device. In this sense, phishing protection is much more of an art than science and refers to a comprehensive set of tools and techniques that can help identify and neutralize phishing attacks in advance. This includes extensive user education that is designed to spread phishing awareness.
Sources
Smear phishing: a new Android vulnerability, jameshfisher.com
An update on our security incident, Twitter