Broadpwn Wi-Fi Vulnerability: How to Detect & Mitigate
It can be easy to think our mobile devices are more secure than they are. However, that is just not the case. In the last three years, there have been dozens of mobile malware creations that have attempted to latch on to our devices with malicious intent. Malware like Pegasus, for example, allegedly spies on both iOS and Android users without their consent.
However, spyware seems a little mild in comparison when you compare it to a bug like Broadpwn.
Learn Vulnerability Management
Until mid-2017 patches were released, a single exploit in an obscure chip helping power billions of devices acted as an open door for a hacker invasion.
That bug was named Broadpwn by Nitay Artenstein, the security researcher who discovered it.
To help understand past and future vulnerabilities of this uniquely-named digital malice, you must first understand what it does to your device.
What Is Broadpwn?
If you want the full, technical and in-depth overview of Broadpwn, I highly suggest checking out Artenstein's original blog post. It is very dense, so wade through at your own risk.
In short, Broadpwn is a worm virus that can be remotely executed on your device without your interaction. All it takes is one knowledgeable hacker on a shared and open Wi-Fi network to place it on your phone.
The result of this worm is the hacker would be able to have total control of your device. They would also be able to use your device as a mobile infection station. Meaning you carry the hacker with you (again, remotely), and they can use your device to breach other devices.
This sounds like the stuff of science fiction, right? Sadly, it is very real.
It works by using a "backdoor" into your operating system (OS). This is surprising because every OS used in smartphones these days is treated like a steel trap of data security.
How Does Broadpwn Work?
Overall, the security of your OS is maintained via two "terms:" DEP and ASLR.
DEP, or Data Execution Prevention, is also known as Executable Space Protection. Think of it as a quarantine for computer viruses attempting to inject code into your operating system.
ASLR, or Address Space Layout Randomization, is another memory protection process for an OS. It acts by randomizing the location where the programs you run are held in memory, thus making it difficult for a hacker to locate where to execute an attack.
Even just one of these elements is enough to frustrate most hacking attempts on your phone's operating system. Moreover, most phones use both.
Broadpwn found a vulnerability in one of the individual hardware elements of the phone. The construction of these parts is often handled by third-party companies, which means the OS makers do not always know everything that's going on with their creation.
Most mobile devices have two chipsets that are interesting to hackers. They are called the Baseband and the Wi-Fi chipset.

As you can see from the image, most attacks are focused on either the Baseband or the Wi-Fi chipset as a way into the application processor, or the OS.
In vulnerable devices, Basebands had security capabilities like DEP. The vulnerable Wi-Fi chipsets lacked both DEP and ASLR.
To make matters worse, the permissions of the chipset also allowed an attacker to read, write and run code anywhere in the chip's memory. This made them an ideal target for an exploit.
Artenstein was also able to find a flaw in some of the versions of the chipset's firmware that allowed his malicious code to work universally.
Because of the lapse in security, Artenstein was able to develop a bug, a remote exploit scheme and an escalation scheme that allowed for what he calls the "first Wi-Fi worm."
In short, Broadpwn can infiltrate a device without any necessary input from the user. An attacker can turn any compromised device into a "mobile infection station."
Why Is It Called Broadpwn?
All these chipsets were created by a company called Broadcom, and "pwn" is computer slang that means "utter defeat." Hence, the name Broadpwn.
Despite this breach, these chips remain the dominant chip in high-end mobile devices. All iPhones after the iPhone 5, all Samsung Galaxies from the S3 to the S8 and all Samsung Note3's, Nexus 5, 6, 6X, and 6Ps were compromised. This list is not exhaustive, however, as it is a very widely used chipset.
To push education on the exploit, Artenstein went on to create his own Three Laws of Remote Exploits (see below).

Broadpwn was a grave threat at the time, but how has this threat fared since its discovery? Moreover, what, if anything, can you do about it?
How Can I Tell If My Device Is Vulnerable or Compromised?
If you have any of the devices, I listed above, there's a high chance you are vulnerable.
Theoretically, at least. I will explain why I say that in a moment.
If you are truly worried about the status of your device, Android users can download an app like the Wi-Fi Chipset INFO app (see below).
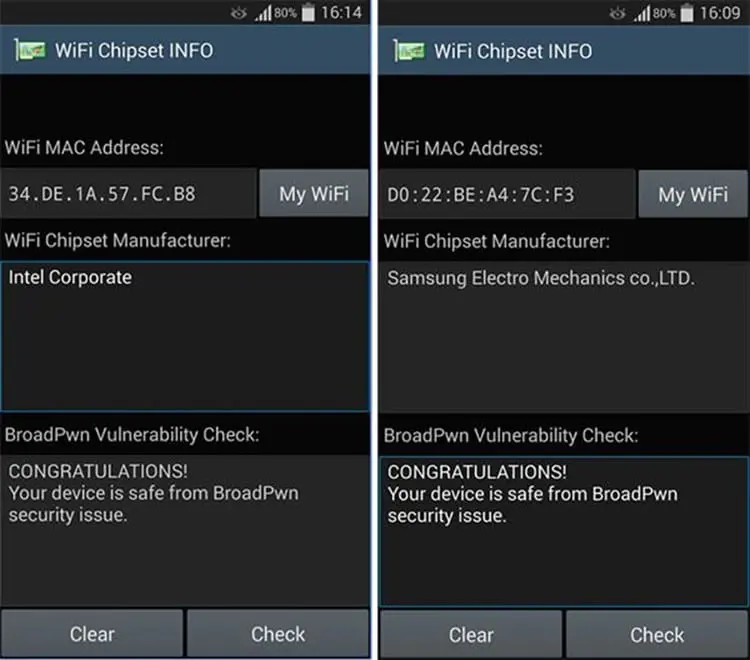
This app only does one thing, but it does it well. Its sole purpose is to determine whether your chipset was one of the vulnerable Broadcom chipsets, and then find out if your device is compromised.
iOS users have a little bit of an easier path toward knowing their chipset. If you have anything later than the iPhone 5, then your Broadcom chipset is vulnerable without the proper updates.
However, just because you are theoretically vulnerable doesn't mean you should panic. There are plenty of steps you can still take to guard your device.
How Can I Keep My Phone Protected from Broadpwn?
In an interview with Wired, Artenstein claimed until the security in the individual pieces of hardware reaches the level of our mobile devices' operating systems, we can continue to expect these types of exploits to pop up.
How do we keep our devices secure, then? Follow these four tips.
1. Keep devices updated
The most significant safety feature with any device will always be to keep your OS updated. So, install new updates as soon as possible.
In the case of Broadpwn, iOS users who downloaded update 10.3.1 in April of 2017 were protected from the possibility of corruption. By July, Apple had the Broadpwn bug on lockdown with update 10.3.3.
Likewise, Android had the bug patched by July.
However, vulnerabilities will always crop up with any electronic device. It is one of the understated risks we all take by carrying these mini-computers in our pockets.

The big takeaway is to always keep your smartphone's operating system up to date. Developers are continually using these updates to push new security features to keep your device ahead of a hacker.
2. Take precautions against all malicious activity
It is always a wise idea when using an electronic device to take certain precautions, e.g., minimizing your location access.
Trend Micro recommends using this technique to help prevent a potentially malware-ridden app from using your device's location for malicious purposes. When your address can be used as part of a financial breach, it is not information you should tread lightly with when you are online.
iOS and Android users have the capability of setting location access to "While Using the App," like below:
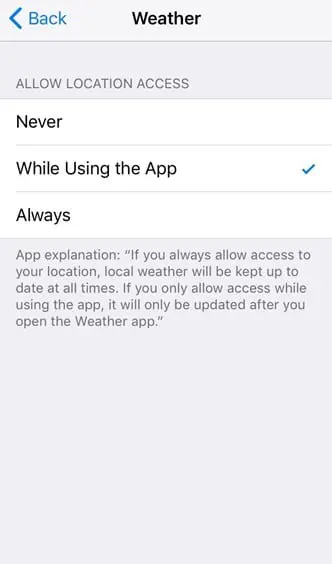
This means killing an app will cut off your location and protect you. If you download an app that doesn't allow this permission, it may be worth deleting it altogether.
A second option for generalized protection is to look for two-fold protection from a VPN with a kill switch like Zenmate.
The VPN can keep your identity protected on open Wi-Fi sources by providing anonymity, while the kill switch acts as a last-ditch defense against being exposed on an untrusted network.
It is a simple and relatively mindless method of protecting yourself while traveling or working from a coffee shop.
3. Only download trusted apps
In mid-2016, Android stated the biggest threat to users was malicious apps downloaded via web browsers or third-party app stores.
While it may limit your options, you should treat your mobile device like you would your personal computer; don't download from an untrusted source.
4. Don't use Wi-Fi on your device
CNET also recommends you could just keep the Wi-Fi feature turned off. That will undoubtedly eat through your data plan if it is not already unlimited.
Your home Wi-Fi is safer, especially if you are following good safety protocol and have a VPN. Don't use a public or open Wi-Fi network that's not encrypting traffic by default.
What Should I do if My Phone is Compromised?
There are dozens of ways to tell if your phone has been hacked. Secure My Social CEO Joseph Steinberg offers these hints:
- Device slowing down
- Sending or receiving strange messages
- Mysterious apps appearing
- Device heating up
- Excessive data usage
- Receiving many pop-ups
Moreover, the list goes on and on. The major takeaway is to be aware of the normal functions of your device simply. That way, when something abnormal starts to occur, you can act appropriately.
What can you do when you know your device is compromised? One option is to run a mobile anti-virus software like McAfee Mobile Security. It is free and helps remove malware while preventing other issues from occurring.
A second method is to simply stay aware of how mobile malware works, be able to recognize it and clean it up before things get bad.
This list from CSO is an excellent summation of some of the more prevalent malware in the last few years, and it is a safe bet that future ones will work similarly.
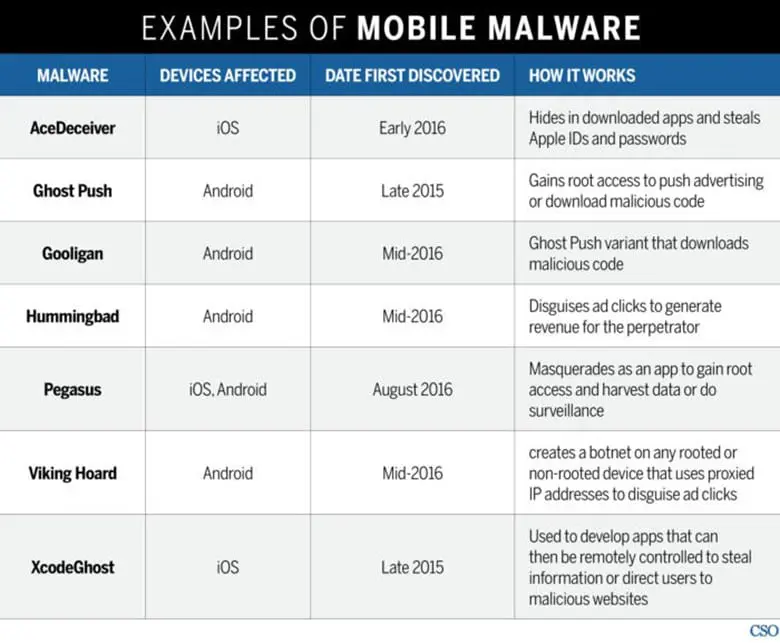
I also recommend keeping tabs on your finances, as many of these attempts are looking to find ways to defraud you and leave you penniless. Report any suspicious findings to your financial institution immediately, and then use a malware remover as I mentioned.
Finally, a less conventional but equally efficient route you can take is to learn how to test the security of the apps you download. You can also find guides that help you learn what ethical hacking is and how to do it.
Final Tips for Mobile Device Security
Digital security will always be a moving target. As technologies continue to advance, hackers will be right alongside it trying to discover new exploits to use against us.
Broadpwn was, and still is, a unique bug. It opened an unparalleled threat and was thankfully closed off in short order. However, does that mean it is not still possible?
I am going to say it probably is possible, and you need to stay ready.
Constantly monitoring your device for signs of attack is the first line of prevention for all users. That should not be your only security feature though. Not by a long stretch.
Remember to keep your device upgraded and start taking precautions now to mitigate the risks of an open Wi-Fi. VPNs, kill switches and limited location services are just the start.
You should also never download anything from an untrusted source. Ever.
Moreover, if you are truly worried about infection, don't use an unsecured Wi-Fi source.
Finally, if your phone is compromised, act appropriately. Use anti-virus services and keep your information as locked down as possible. The sooner you discover and eliminate a leak, the safer you will be.
Learn Vulnerability Management
At the end of the day, Broadpwn is the first wave of many attacks like this. Will you be ready for the next attack?






