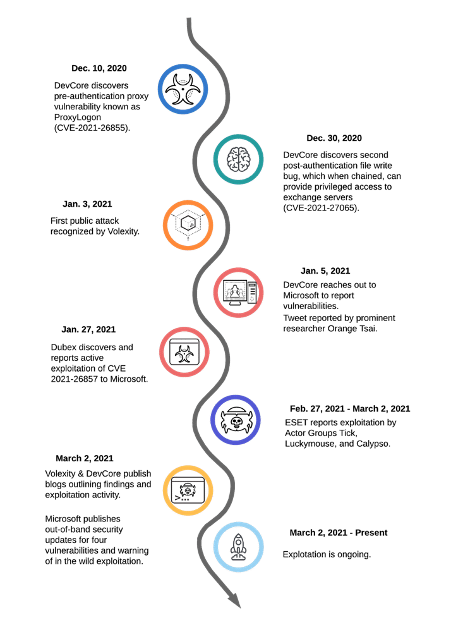How criminals have abused a Microsoft Exchange flaw in the wild
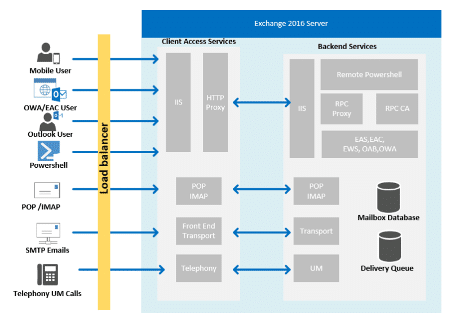
As noted by Keysight and others, Microsoft Exchange servers have a specific block architecture designed to handle high loads and provide availability and communication between different server versions. For example, multiple exchange servers running the same version could be configured to work using a database availability group (DAG) to provide database-level recovery from failures.
Figure 1: Exchange architecture high-level diagram.
Each Exchange server operates in multiple layers of protocols that are used to provide access to various resources. External client apps don’t communicate directly with the back-end service for obvious reasons, but all of these systems interact with front-end APIs such as Outlook Web App (OWA).
Because of this segregation between the backend and client layers, a proxy is used as a middleware agent to pass requests between OWA (running on port 443 TCP) and the exchange backend that is bound to port 444 TCP. This flow is assured by the library ‘Microsoft.Exchange.FrontEndHttpProxy.dll’ that operates as an IIS module.
Learn Vulnerability Management
The story of CVE-2021-26855 starts here, where a researcher from DevCore, a Taiwan-based security consulting firm, began a project to explore the problems and security of Microsoft Exchange Servers. In just two months of research in 2020, researchers discovered a critical unauthenticated vulnerability called ProxyLogon that could be exploited in the wild by criminals around the world to get remote code execution on the vulnerable servers.
Figure 2: The researcher credited with the discovery of the vulnerabilities tweeted publicly.
After this discovery, a second flaw was identified that could be chained together with the ProxyLogon vulnerability to gain privileged access to Exchange Servers and write files into the server. This second vulnerability is now known publicly as CVE-2021-27065.
In a timeline of activity by PaloAlto presented below, we can understand the exploitation chain since its discovery to the exploitation in the wild by criminals.
Figure 3: High-level timeline of activity by PaloAlto (source).
CVE-2021-26855 and CVE-2021-27065 walkthrough
CVE-2021-26855 is an SSRF vulnerability, and the problem occurs when proxying client requests to the server. This vulnerability can obtain the user’s sid, which is the most important first step in a non-interactive attack chain. On the other hand, the CVE-2021-27065 is a file writing vulnerability. Criminals can abuse this to write a malicious file into the remote server, a web shell for instance, and execute it remotely to gain high privileges and code execution.
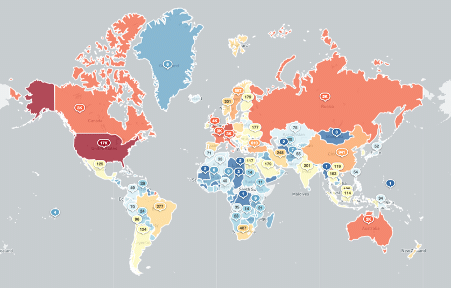
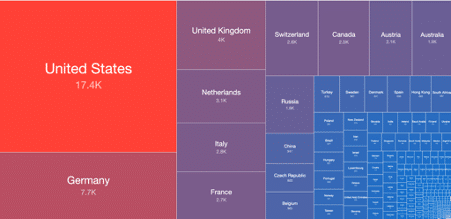
From the ShadowServer survey, we can observe that many Exchange servers are still vulnerable around the globe, including the U.S. with 17,400 vulnerable servers, Germany 7,700 thousand and the UK 4,000.
Figure 4: Exchange servers vulnerable to the ProxyLogon flaw (source).
Digging into the details: CVE-2021-26855
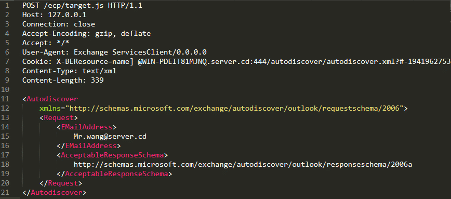
The authentication bypass vulnerability results from having to treat requests to static resources as authenticated requests on the backend because files including scripts and images must be available even without authentication. With this in place, the flow is triggered by using a cookie named X-BEResource that has the following format:
From here, the proxy takes the host part and concatenates it to the request path to create the fill URL request to communicate with the backend. Figure 5 below demonstrates how this vulnerability can be executed.
Figure 5: Malicious post request with the manipulated X-BEResource parameter.
The concatenation process is performed in the Microsoft.Exchange.FrontEndHttpProxy.dll DLL, and after some permutations, the researchers found a bypass using a tild character (~) to create a target and crafted payload.
After that, an attacker is free to send arbitrary requests to obtain a valid and authenticated OWA session.
From this point, the valid session can be used by malicious actors to explore other authenticated vulnerabilities, such as CVE-2021-26855, to obtain remote code execution, deploy ransomware or proceed with double extortion tactics.
Exploring CVE-2021-26855
The CVE-2021-26855 is a chained vulnerability, and an attacker just needs a valid admin mail exchange account to proceed with this exploitation phase.
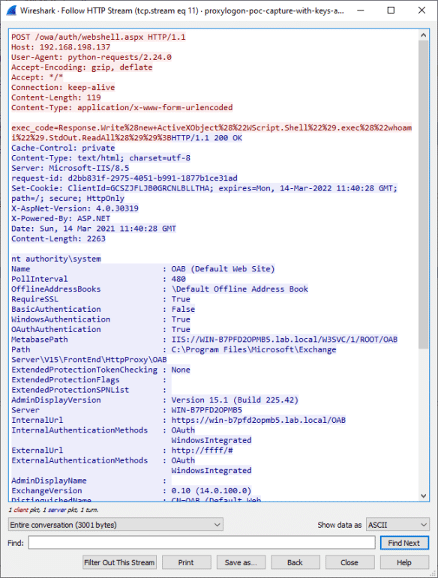
Several exploits were published on GitHub last few months, and several organizations around the world were severely impacted. Criminals can write into the vulnerable servers’ web shells to guarantee post access.
Figure 6: Wireshark with the request to a web shell file implanted on the target exchange server.
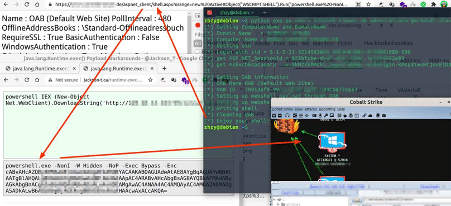
As also mentioned by Seguranca-Informatica, criminals have used CobaltStrike beacons to get remote connections and implant other kinds of threats, such as ransomware.
Figure 7: ProxyLogin exploitation - webshell + cobaltstrike.
Learn Vulnerability Management
The threat of ProxLogon
The ProxLogon chain is probably the most critical vulnerability impacting Exchange Server in recent years. With ProxyLogin in place, criminals can deploy web shells into the vulnerable server, cryptominers and also ransomware (DearCry).
In this way, the best and most complete mitigation for this threat is to update to a supported version of the Exchange Server and also ensure it is fully updated. On March 3, 2021, Microsoft released out-of-band patches for Microsoft Exchange Server 2013, 2016 and 2019.
Sources:
- ProxyLogon timeline, PaloAlto
- A look at the ProxyLogon Microsoft Exchange vulnerability (CVE-2021-26855), Keysight
- ProxyLogin technical details, Segurança-Informática