How to discover open RDP ports with Shodan
Remote desktop protocol (RDP) allows you to connect to remote computers for administration through a remote desktop client to administer servers and systems. This protocol is generally discouraged because various exploits are designed to abuse it and because many technical teams do not know how to secure it very well. However, with the recent COVID-19 pandemic and many people still working from home, there has been a recent rise in RDP adoption across organizations.
Learn Vulnerability Management
What is Shodan, and what is it used for?
Shodan is a search engine for internet-of-things devices across the internet. Unlike Google, Shodan does not index files and search for keywords online. It instead searches for ports and services on IP addresses of internet-connected devices. Shodan can identify devices on the internet based on several characteristics. For example, it searches for devices on the internet based on their banner information, geographical and GPS location, firmware version, device type, software version, protocol version and so much more.
Hackers love Shodan because they can use it to discover targets to exploit. Such targets could, for instance, include industrial control systems that are running very specific software versions, internet-of-things devices such as TVs, unprotected cameras that are live streaming, FTP servers with sensitive information and even when the worst comes to worst, Very Small Aperture Terminals (VSATs) on naval vessels.
How does Shodan work?
Shodan works by crawling the internet constantly 24 hours a day, seven days a week. The crawling, however, does not sweep through IP address ranges like a network scanner such as Nmap or MassCAN would. The Shodan crawlers attempt to perform a full protocol-specific handshake to determine whether a port is open or closed. Since there are numerous measures to spoof ports, Shodan implements several measures to ensure that the port that it is reporting is indeed open. For example, in the case of RDP, Shodan takes a screenshot of the discovered open RDP port, performs optical character recognition on the captured screenshot and performs various security checks to determine whether you can hack into RDP.
What is Remote Desktop Protocol, and what is it used for?
The Remote Desktop Protocol (RDP) is a protocol used by system administrators to remotely administer their Windows servers or workstations. This requires an RDP client that remotely connects to the RDP server, the Windows machine.
RDP has spiked in recent times due to the COVID-19 pandemic that has forced many to work from home. Malicious hackers are now targeting publicly exposed RDP ports in attacks against newer versions of RDP. In the following sections, we discuss how you can use Shodan to discover open RDP ports for yourself.
Discovering open RDP ports using Shodan
Before we can begin searching for open RDP ports, we need to familiarise ourselves with two significant features of Shodan, namely facets and filters.
Facets display a detailed view of the most frequent global information. It would help if you remembered that these usually change depending on the search applied. These will appear on the left side of the screen and will include:
- Total results. This displays the total number of hits from the search that has been executed.
- Top countries. This displays the countries in which the search returns hits.
- Top organizations. This displays the organizations that are affected by the hits from the search.
- Top products. This displays the products related to the hits from the conducted search.
- Top operating systems. This displays the operating systems affected by the search that is conducted.
On the other hand, filters help you drill down to a more granular view of the hosts you would like to inspect. The following are some of the filters that you can use:
- City – this is how you specify the name of the city.
- Country – this is a two-letter code, and it is how you specify the country.
- Has_screenshot – with this, you can specify the screen image.
- OS – this is how you specify the operating system.
- Port – this is how you specify the port.
- Product – this is how you specify the product.
- State – you can specify the state in which you want to search for devices.
- Version – this is how you specify the version of the service you are interested in.
You should note that the search results might vary greatly depending on the filter that has been used.
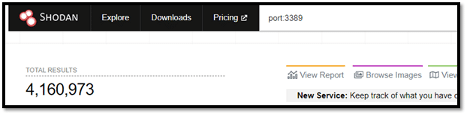
To begin searching for open RDP ports, you can input the following into the search bar: port:3389.
The filter above returns all of the hits discovered by Shodan as having the default RDP port 3389 open. As we can see below, there are a total of 4,160,973 results.
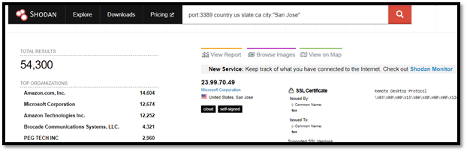
We can drill down further by applying more filters. We can add the following: country:us state:ca city:”San Jose.”
This specifies the country as the United States of America, state as California and city as San Jose. See the screenshot below. Note that the double quotes are used since the value we are specifying has a space character.
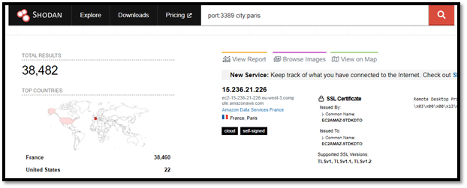
Doing this greatly reduces the total results to 54,300. You can drill down further by issuing an area code or postal code if you have one. However, sometimes you could search for a city and receive more than one location, say for instance, we search for RDP ports in the city of “Paris.”
This is shown below:
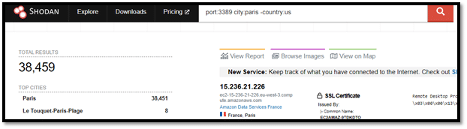
We quickly realize that there are two countries with the city Paris. To remove the USA from the facets, we use “-country:us”. That is, we include a minus sign in front of the country filter as shown below:
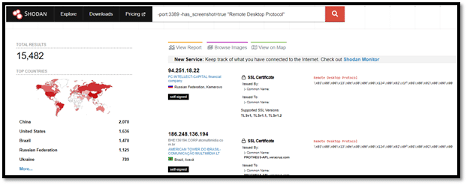
We can use a trick to identify RDP servers that are running on elevated ports. To do this, we would need to use the following filter: -port:3389 -has_screenshot=true "Remote Desktop Protocol."
This simply tells Shodan to ignore everything on port 3389, which is the default RDP port, ignore any screenshots, but then look for the text string “Remote Desktop Protocol”. This results in results similar to the following:
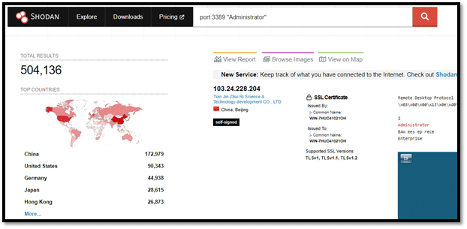
You can also find the user accounts related to RDP by appending the username beside the port filter, as shown below.
Doing this results in the following screenshots exposing administrator accounts within RDP.
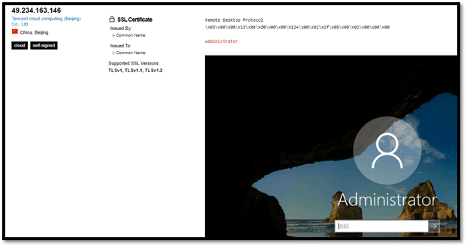
The screenshot above shows a Windows machine in Beijing, China with the Administrator account prompting a login password.
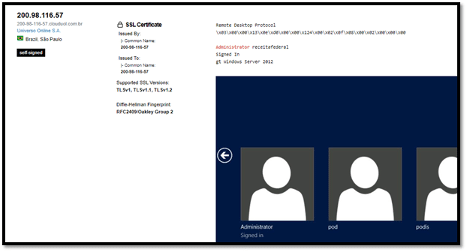
The screenshot above shows a Windows machine in Sao Paulo, Brazil, with two more accounts besides the administrator account. A malicious hacker could at this moment begin launching attacks against the other revealed user accounts.
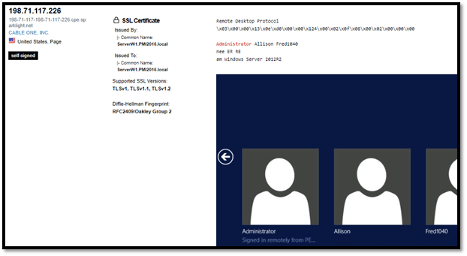
Finally, the screenshot below shows a Windows server in the United States of America with the administrator account and two more.
You should ensure that RDP is disabled for remote use since, as we have seen, simply elevating to a non-standard RDP port does not prevent Shodan or hackers using it from discovering open RDP ports.
Learn Vulnerability Management
Utilizing Shodan
In this article, we have discussed what Shodan is and why it is used. We have seen that remote desktop protocol is still in use today despite the numerous attacks against it over the years. We have also discussed how Shodan can be used to discover open RDP ports across the globe and how performing quick fixes like elevating to a higher port (non-standard RDP port) does not resolve the issue. It’s important to ensure that RDP is disabled for remote administration and move toward more secure methods of remote workstation administration.
Sources:
- Trends in Internet Exposure, Shodan
- Quick Guide: How to Use Shodan, Authentic8
- Learning How to Use Shodan with RDP, Sentandsecure