HTTPS and mixed content vulnerability
HTTPS is used to make communication between the server and the browser secure. However, a problem occurs when an HTTPS page loads HTTP content: this is called mixed content vulnerability. There are two types, active and passive, discussed in this article. Finally, a demo page with this vulnerability is presented along with an exemplary detection method.
Learn Vulnerability Management
SSL/TLS – protecting the communication channel
First, we need to answer the following questions before discussing mixed content vulnerability:
- What is protected by HTTPS?
- What security properties are offered by HTTPS?
- What is the difference between HTTPS and HTTP?
HTTPS uses SSL/TLS, which works between the application and the transport layers of the OSI model. SSL/TLS is used to protect the data of the application layer.
The following properties are achieved when HTTPS is used: authentication, data integrity, confidentiality. This is fine for protection of data in the communication channel between the server and the browser.
The problem appears when an HTTPS page loads HTTP content – HTTP is insecure, and attackers can read/modify HTTP traffic.
HTTPS page loading HTTP content
Protection of the communication channel between the server and the browser is one issue. Another issue is the content that is sent in this channel.
Imagine an HTTPS page that loads the script over HTTP (mixed content vulnerability). Then the browser sends an HTTP request to get this script. Remember that HTTP is insecure – the attacker can read or modify the traffic. Let's assume there is an attacker in the middle of the communication. The attacker sees the request and waits for the response from the server. When the response comes, the attacker modifies it and forwards to the user's browser. This is how a man-in-the-middle (MITM) attack works. As a consequence, the content of the attacker's choice is executed in the user's browser.
Mixed content vulnerability (passive and active)
Let's consider two cases – an HTTPS page which loads an image over HTTP (the first case), and an HTTPS page which loads the script via HTTP (the second case).
Let's discuss the first case. When the image is loaded over HTTP, the attacker can change this image. As a result, the appearance of the site is influenced. This is not very dangerous, because the attacker doesn't change the behavior of the HTTPS page. However, data integrity is not preserved. This is an example of mixed passive content.
Let's now discuss the second case. This is a more dangerous scenario, because changing the script affects the behavior of the HTTPS page. This is an example of mixed active content.
Demonstration and detection of mixed content vulnerability
Microsoft prepared a demo with mixed content vulnerability [1] – you can go there and play with it (the certificate is invalid at the moment of writing this article, but it doesn't matter from the perspective of mixed content vulnerability demonstration). You will also need a proxy to see requests/responses and tamper with responses (simulation of MITM attack). You can use Burp Proxy for this purpose. Burp Proxy is a part of Burp Suite, which is an integrated platform for web site security testing [2]).
It turns out that the aforementioned HTTPS demo page loads the script via HTTP (just take a look at the source of this site).

However, you don't have to do this analysis manually. You can use the Opera browser, for example, to see the mixed content vulnerability warnings (go to the Console in Developer Tools). Below I present them for the aforementioned demo page (mixed active content in the red frame; the rest is mixed passive content).
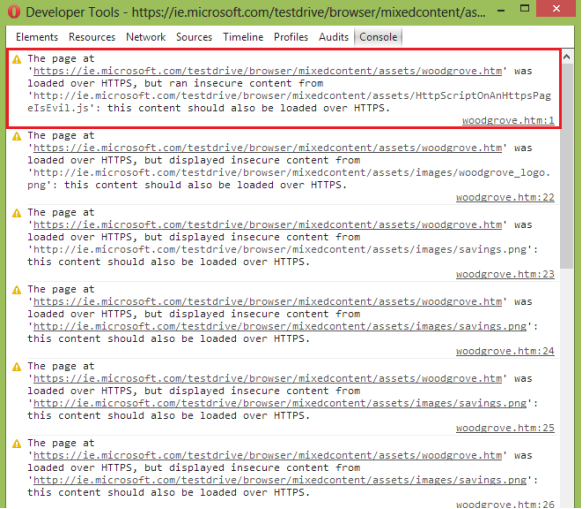
Summary
HTTPS is used to protect the data of the application layer of the OSI model. However, the problem appears when the HTTPS page loads HTTP content, also known as mixed content vulnerability. Because HTTP is not secure, the attacker can launch a MITM (man-in-the-middle) attack. As a consequence, the attacker has an impact on the HTTP content that is delivered to the user's browser.
Two types of mixed content vulnerability were discussed – mixed active content (it can change the behavior of the HTTPS page) and mixed passive content (it doesn't change the behavior of the HTTPS page, but affects its integrity). Finally, it was presented how the Opera browser can be used to detect mixed content vulnerability.
Finally, don't hesitate to contact me on Twitter (@dawidczagan) if you have any questions or want me to discuss other security topics of your interest.
Learn Vulnerability Management
Sources
- Mixed content vulnerability – demo page prepared by Microsoft
- Burp Suite






