SonicWall firewall VPN vulnerability (CVE-2020-5135): Overview and technical walkthrough
A critical stack-based buffer overflow vulnerability was discovered in SonicWall Network Security Appliance (NSA) VPN. In this article, we will address the problem explored by this flaw, its impact worldwide and mitigation measures to fix the problem and avoid cyber-incidents using this specific vector as an entry point on the internal infrastructure.
Learn Vulnerability Management
CVE-2020-5135: Overview
The flaw can be triggered by an unauthenticated HTTP request involving a custom protocol handler. The vulnerability leverages the HTTP/HTTPS service used for product management as well as SSL VPN remote access. This service can be exploited to cause a denial-of-service condition and possibly remote code execution.
Nikita Abramov of Positive Technologies and Craig Young of Tripwire’s Vulnerability and Exposures Research Team (VERT) discovered CVE-2020-5135. This flaw affects the following versions of SonicOS:
SonicOS 6.5.1.11-4n and earlier
SonicOS 6.0.5.3-93o and earlier
SonicOSv 6.5.4.4-44v-21-794 and earlier
SonicOS 7.0.0.0-1According to the researchers, the vulnerability resides in a pre-authentication and in a component SSLVPN, which is often exposed to the public internet. This opens the doors to possible attacks in the wild.
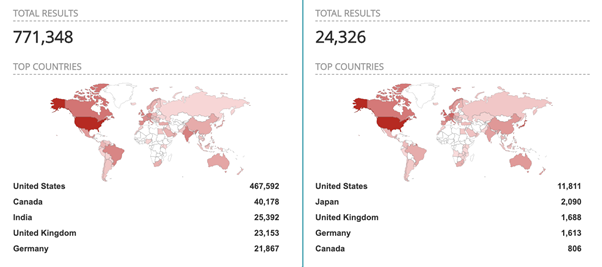
Impacted devices by number
The number of exposed devices on the internet is huge, and nearly 800,000 hosts may be vulnerable. This number is based on a Shodan search for the HTTP banner of the SonicWall firewall.
The Tenable team doesn’t confirm that the hosts found on Shodan were affected by this particular vulnerability.
“The hosts discovered with our Shodan queries are indicative that they are internet facing SonicWall servers, their respective versions could not be determined and thus it is unclear if they are vulnerable.”
With this set of information in place, criminals could abuse a DoS condition — which is easy to obtain, as the attack only requires a successful connection with the affected device. The malicious payload can be used to trigger the flaw on the SSL VPN portal.
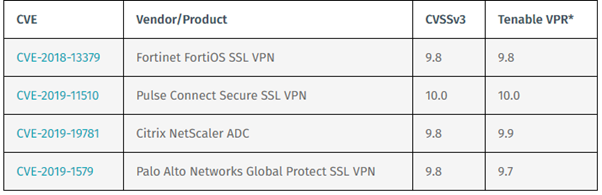
Looking at the last year, we can find a set of vulnerabilities present and explored by criminals in SSL VPN solutions. As these kinds of devices are the edge of the internal network with the public internet, they are an enticing target for criminals. As VPNs take an increasingly important role amidst the rise in working remotely, exploitation of these devices can allow criminals to pivot to an internal network and begin targeting the entire ecosystem.
As observed below, some notable vulnerabilities were found in VPN devices from several vendors last few years, including:
Mitigation measures
With CVE-2020-5135 in place, attackers potentially have another SSL VPN vulnerability in scope to target vulnerable systems. In this way, patching the affected versions is mandatory in order to fix the problem.
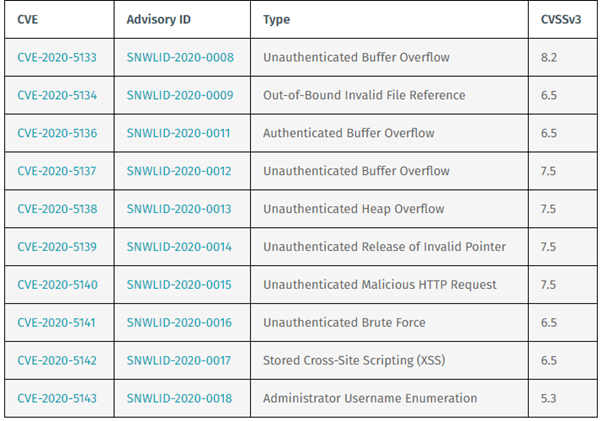
In total, SonicWall patched 11 vulnerabilities on October 12th, 2020. The following table lists the remaining 10 vulnerabilities that were patched:
All of the vulnerabilities were discovered by security researcher Nikita Abramov of Positive Technologies Offensive Team. Abramov is credited with discovering CVE-2020-5135, along with Craig Young of VERT.
Learn Vulnerability Management
At the moment of writing this article, no public exploit or PoC was published online.
More details about this vulnerability can be found here:
Sources
SonicWall VPN Portal Critical Flaw (CVE-2020-5135), Tripwire
Vulnerability List, SonicWall
If you want to practice writing exploits and worms, there's a big hijacking hole in SonicWall firewall VPNs, The Register
CVE-2020-5135: Critical SonicWall VPN Portal Stack-based Buffer Overflow Vulnerability, Tenable