Turla Crutch backdoor: analysis and recommendations
Crutch is a newly discovered backdoor from Turla advanced persistent threat (APT), a Russian-linked threat actor, used in a recent cyberattack against an country’s Ministry of Foreign Affairs. The attack leveraged Dropbox to exfiltrate sensitive documents. Let's explore how to protect end users and network assets against threats of this nature.
Learn Vulnerability Management
What is Turla Crutch backdoor?
Turla APT has been active for over 10 years, compromising several governments and diplomatic entities around the globe. Recently, Enjoy Safer Technology (ESET) researchers found a new backdoor dubbed Crutch used to exfiltrate documents and sensitive information. “According to our research, it was used from 2015 to, at least, early 2020. We have seen Crutch on the network of a Ministry of Foreign Affairs in a country of the European Union, suggesting that this malware family is only used against very specific targets as is common for many Turla tools,” said ESET.
Given the similarities found between a Crutch dropper and Gazer, also known as WhiteBear, which was disseminated and used by Turla APT, there is a strong probability this backdoor is part of the group arsenal.
By analyzing the two samples, ESET found the following similarities:
- Both samples were dropped on the same machine in September 2017
- The samples drop CAB files containing the various malware components
- The PDB paths are very similar
- The loaders decrypt their payloads using the same rivest cipher 4 (RC4) key
Discovering Crutch backdoor
Crutch is a potent backdoor used by Turla APT against several machines of the Ministry of Foreign Affairs in a country of the EU. This backdoor was developed with capabilities to exfiltrate sensitive documents and other sensitive files to Dropbox accounts that Turla criminals control. With this technique in place, criminals can bypass security measures by abusing legitimate tools to hide the malware behind normal network traffic.
In general, the main activity of this threat group consists of three scenarios:
- Internal network reconnaissance
- Lateral movement
- Espionage
During the exfiltration process, the backdoor communicates with the C2 server — the Dropbox accounts — and gets some ZIP archives. These ZIP archives contain inside commands for the backdoor, uploaded to Dropbox by the Crutch operators. The commands include the operations performed by the backdoor, namely:
- Compressions of files
- Set up the staging
- File exfiltration
- Remote command execution
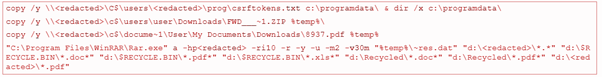
Next, some operations used by the backdoor during its chain are presented below.
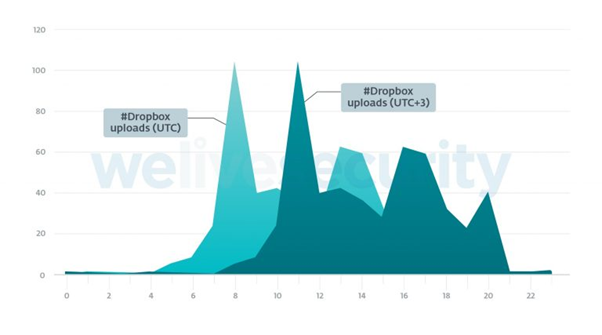
ESET collected 506 different time stamps and they range from October 2018 to July 2019. The next plot presents the operator’s activity — Dropbox uploads — during the data exfiltration operation.
From the graphic, it is possible to see that criminals are working in the UTC+3 time zone.
Crutch version 1-3 and 4
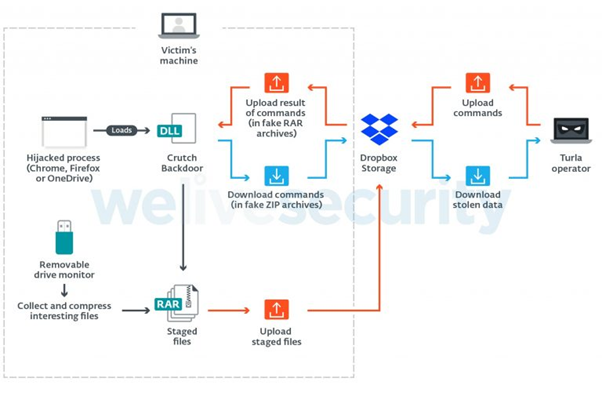
Crutch version 1-3 from 2015 to mid-2019 used a backdoor communicating with Dropbox and a drive monitor without network capabilities.
The high-level diagram of this version is presented in the next image. According to ESET, “It includes a backdoor that communicates with a hardcoded Dropbox account using the official HTTP API and executes basic commands such as reading and writing files or executing additional processes.”
Persistence is achieved via DLL hijacking on several systems such as Google Chrome, Firefox and OneDrive.
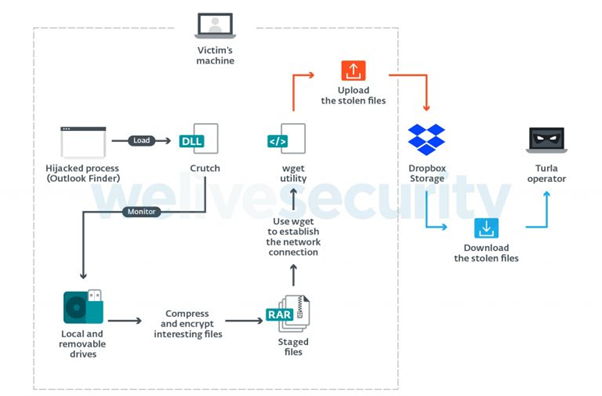
More recently, in July 2019, a new version of this backdoor was released: Crutch 4. This new version is an updated version of the removable-drive monitor with networking capabilities.
As observed from the following diagram, the main difference is that this new version no longer supports backdoor commands. Instead, Crutch can autonomously upload the files found on local and removable drives to Dropbox by using the Windows version of the Wget tool (LOLBins).
The backdoor is stored on C:\Intel folder, with some artifacts inside:
- dll: The Crutch DLL
- exe: The genuine Outlook Item Finder from Microsoft Outlook
- dll: Genuine DLL that is a dependency of finder.exe
- dat: Crutch config file. It contains the Dropbox API token
- exe: The genuine RAR utility
- exe: A clean version of the Wget utility for Windows
Using legitimate tools during the Crutch activity such as “msget.exe” will minimize the risk of detection bypassing, thus, internal defenses, antivirus and EDR systems.
Learn Vulnerability Management
The threat Crutch poses
Crutch backdoor can bypass security perimeters by abusing legitimate tools and Cloud infrastructure like Dropbox. With these capabilities, it can mask its network traffic while exfiltrating stolen information and receiving commands from its operators.
Updating systems and using antivirus engines is mandatory to fight this problem. Using network monitorization to find potential strange behaviors or abnormal traffic on the network is also important.
The use of strong and complex passwords both in accounts or network devices such as computers, servers, routers and switches, and changing the default user account to access those devices, is also a good way to prevent lateral movement activity.
Lastly, enable multi-factor authentication whenever possible to prevent unauthorized access to critical systems and avoid exfiltration and access to sensitive information.
Sources:
Turla Crutch: Keeping the "back door" open, Welivesecurity by ESET (https://www.welivesecurity.com/2020/12/02/turla-crutch-keeping-back-door-open/)