Unpatched address bar spoofing vulnerability impacts major mobile browsers
Introduction
A number of web browsers have been affected by an address bar spoofing vulnerability that could lead to malware infections and successful spearphishing attempts. The issue is of particular gravity as it also affects major browsers in the mobile environment, ranging from Safari to Opera, Rits, Bolt and UCWeb.
Learn Vulnerability Management
What is address bar spoofing?
Ever since the early days of the internet, Web browsers have been targeted by attackers who use the user interface (UI) to trick computer operators. Address bar spoofing is a technique used by phishers to disguise the URL of a malicious page they want the user to visit, making it look like the intended landing page. Information and its source are obscured or spoofed.
This type of vulnerability is also listed on the Common Weakness Enumeration list as CWE-451 since 2006 (together with a long list of examples) and is definitely a cause for concern. Attackers able to spoof the URL address bar could lure online users into surfing a dangerous website, stealing account credentials and credit card information or attacking with malicious code.
Security researchers are more and more discovering phishing campaigns that utilize this scheme; even by simply using slightly misspelled URLs, malicious hackers can make it difficult for users to recognize the redirection from the original to a spoofed URL. Ignoring this threat could result in painful consequences for victims, their devices and the networks they operate on.
How does it work? While the browser is pointing to the page requested by the user, a JavaScript code redirects to another page created by a malicious hacker.
Security researcher Rafay Baloch explains an example: "the vulnerability occurs due to Safari preserving address bar of the URL when requested over an arbitrary port, the set interval function reloads bing.com:8080 every 2 milliseconds and hence user is unable to recognize the redirection from the original URL to spoofed URL." It is then easy to trick the operator who, believing to have landed on a reputable, safe website, can release sensitive information. This leads to data compromise, as well as giving access to malware on the network.
According to Arif Khan, who found and reported the flow in the UC Browser apps for Android, this issue “is happening primarily because some mobile browsers are using bad regex checks. They are trying to enhance user UX by displaying only search terms when the user searches for something on search engines like Google.” They check whether the site visited starts with www.google.com and if so, checks are skipped.
As seen in a UC Browser Security Advisory, just by using a string like www.google.com.blogspot.com and then attaching the target domain name to the query portion of this subdomain like ?q=www.facebook.com, the attack becomes almost undetectable.
Researchers like Arif Khan believe that URL address bar spoofing is the worst kind of phishing attack possible. This is because it undermines the ability to identify the site visited by the user and works by banking on a false sense of security.
What happens if address bar spoofing is used?
Address bar spoofing vulnerabilities in mobile browsers is becoming one of the prevailing security threats. When address bar spoofing is used, it can lead potential victims to access malware phishing sites or malvertising landing pages. The victims, who are already somewhat less guarded when browsing through mobile devices, can be easily persuaded to share sensitive information, insert credentials and pave the way to malware insertion.
Mobile devices, in fact, normally offer less-evident security features and messages. They also have smaller screens, which prevent users from fully taking note of warning and redirects.
But the users are not the only victims. This type of vulnerability is also able to trick anti-phishing solutions in browsers. It also can exploit the time lag between the page loading and the address bar refresh by quickly introducing false pop-ups or entire pages of made-up content. Users believe they are visiting the correct, safe page and therefore think that any request for info or credentials is perfectly legitimate.
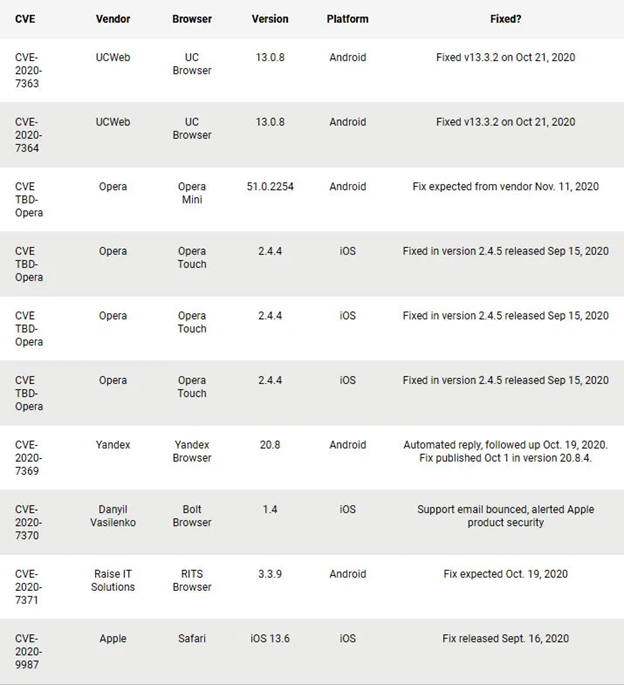
Once alerted by researchers in summer 2020, most companies immediately moved to counteract the vulnerability by releasing patches.
Image 1: Patches for address bar spoofing (source: TechLog360)
However, some are still unfixed and continue to pose a threat to users and systems.
How can an organization prevent becoming victims of these malicious schemes? The first countermeasure is to apply a zero-trust approach. In an environment where spoofing is possible, a zero-trust approach means that connections must be verified and everyone authenticated and authorized when accessing data and apps. Zero-trust means exactly that: no one is a trusted source and no one is a trusted user.
In view of this approach, an important means of protection is also multifactor authentication (MFA) that requires the use of more than one means to identify an authorized user. In addition to a password, one or more verification items are included: for example, security questions, biometrics, PINs and phone checks may be necessary to verify the user’s identity and increase the security of the network.
In addition to this important measure, how can users also become a barrier to spoofing? First of all, the key to preventing address bar spoofing attacks is awareness. The more users know of these schemes and their application, the better they can try to spot issues when browsing.
The second countermeasure is obvious: keeping the browser always updated to the last release by downloading and installing all patches provided; keeping all software, especially web browsers, up to date is crucial to help prevent such attacks. If a known vulnerability has not been addressed satisfactorily, operators should discontinue the use of the affected app until the issue is resolved.
Learn Vulnerability Management
Conclusion
It has been definitely important to discover and patch the summer 2020 mobile browser vulnerability. As it also affected major apps, it could have potentially involved millions of users.
As other similar vulnerabilities will likely be discovered in the future, it is essential that users are aware of this threat and place more attention than ever to signs that something is not right during their browsing activities. An important role is played by consistent updating of apps, as well as the use of MFA and a zero-trust approach especially when the protection of sensitive data is concerned.
Sources
Multiple Address Bar Spoofing Vulnerabilities In Mobile Browsers, Rafay Baloch
Seven mobile browsers vulnerable to address bar spoofing attacks, ZDNet
Mobile Browser Bugs Open Safari, Opera Users to Malware, Threatpost
UC Browser for Android Vulnerable to URL Spoofing Attacks, BleepingComputer
Popular Mobile Browsers Are Vulnerable To Address Bar Spoofing, TechLog360
Safari, other mobile browsers affected by address bar spoofing flaws, Help Net Security
Vulntober: Multiple Mobile Browser Address Bar Spoofing Vulnerabilities, Rapid7
A Set of Address Bar Spoofing Vulnerabilities in Mobile Browser, GlobalHackNews
URL address spoofing flaw keeps mobile victims from determining fake, real sites, SC Magazine
Popular Mobile Browsers Found Vulnerable To Address Bar Spoofing Attacks, The Hacker News
Safari Among Seven Mobile Browsers Affected by Address Bar Spoofing Vulnerabilities, SmartTechGuys