vSingle is abusing GitHub to communicate with the C2 server
Criminals have used various methods to obfuscate a malware’s internals: its information, C2 configuration, TTP, etc. In particular, Lazarus' advanced persistent threat (APT) operations are characterized by using malware specially crafted for attacking financial institutions, espionage, and disruptive purposes. Several campaigns have been carried out against the U.S., Israel and other countries as part of offensive and massive attacks by the Lazarus group.
Technical details
A few weeks ago, the vSingle malware from the Lazarus arsenal was updated with many features, including a command and control (C&C) method based on GitHub pages. vSingle traditionally appears in the form of a PE file (.exe) that loads into the memory of a target DLL. vSingle is a multi-architecture malware, distributed both for Windows and Linux operating systems, as shown below.
Figure 1: ELF VSingle (Linux) and VSingle Windows version
Obfuscation routine
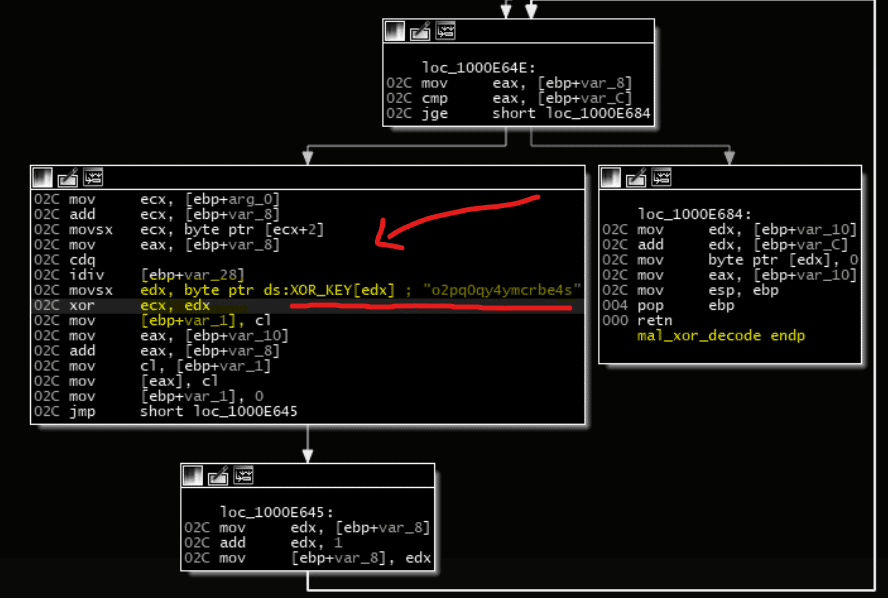
This malware uses a simple XOR to obfuscate its strings with a fixed key. In Figure 2 below, we see the key “o2pq0qy4ymcrbe4s” is used to deobfuscate the malware string in runtime.
Figure 2: String obfuscation of vSingle malware
Some vSingle plain-text strings can be seen in the next table.
[+] Download Parameter Error
[+] Download Result
[+] Upload Result
[+] Upload Parameter Error
[+] Interval Interval was set to
[+] Plugin Download Result
[+] Update
[+] Info
[+] Uninstall Valefor was uninstalled successfully.
[+] Executable Download Result
[+] Executable Download Parameter Error
[+] Plugin Execute Result
Malware commands
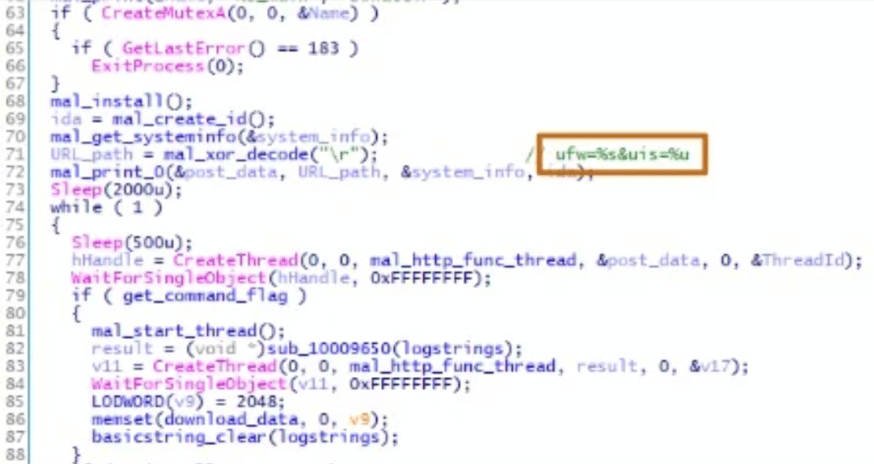
VSingle is released by Lazarus APT with eight internal commands, namely:
- file upload
- communication interval
- execute shell commands
- download and execute the malware plugins
- update itself
- malware information transmission
- uninstall itself
- file download
In addition, vSingle uses four types of plugins that can be downloaded into the target machines and executed, including:
- Windows executable (saved as a .tmp file)
- VBS file (saved as a .vbs file)
- BAT file (saved as .bat file); and
- Shellcode format
VSingle GitHub C2 communication
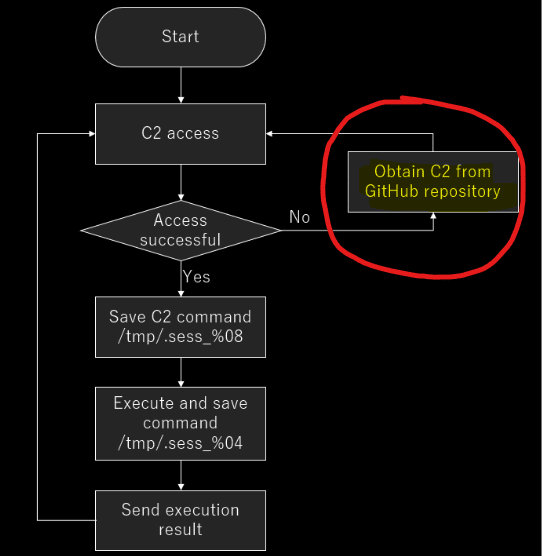
The latest release of this malware takes advantage of several GitHub repositories to perform its operation. Figure 3 below highlights the new feature published by JPCERT/CC analysis.
Figure 3: High-level diagram of VSingle malware (source)
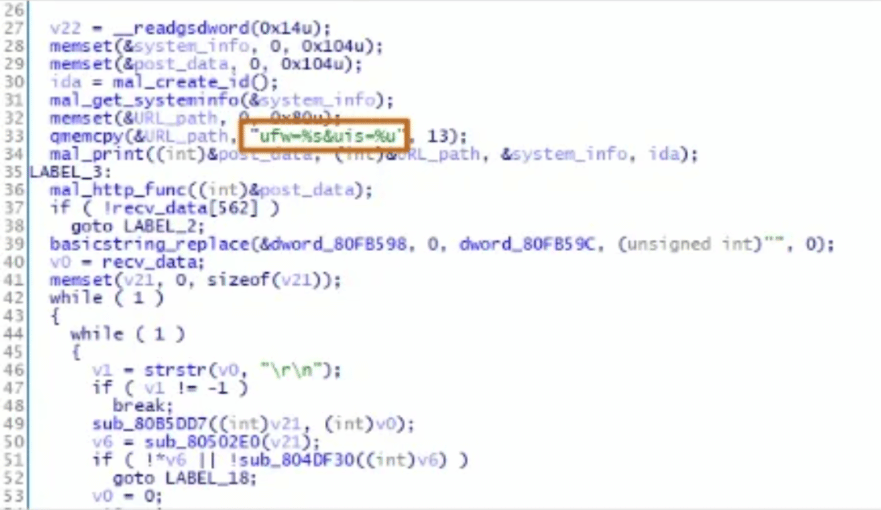
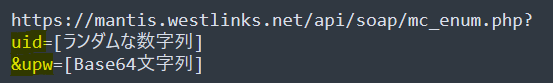
The first packet sent to the C2 server has two PHP parameters, uid and upw. The first one contains a hash value of the target hostname, kernel release number, and IP address. The upw contains a Base64-encoded string of "[IP address]|30.0|12b"
Figure 4: First communication of vSingle malware
The data received from the C2 server, including the RC4 key, are stored in the /tmp directory (/tmp/.sess_%08x), as illustrated in Figure 3.
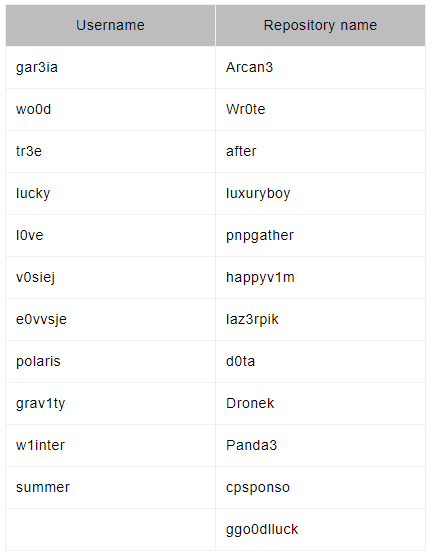
The GitHub endpoints are generated dynamically during the malware execution. According to the JPCERT/CC analysis, the username and repository used by the malware are obtained from this list during the execution.
(source)
The values are then replaced in the following path:
https://raw.githubusercontent.com/%s/%s/master/README.de
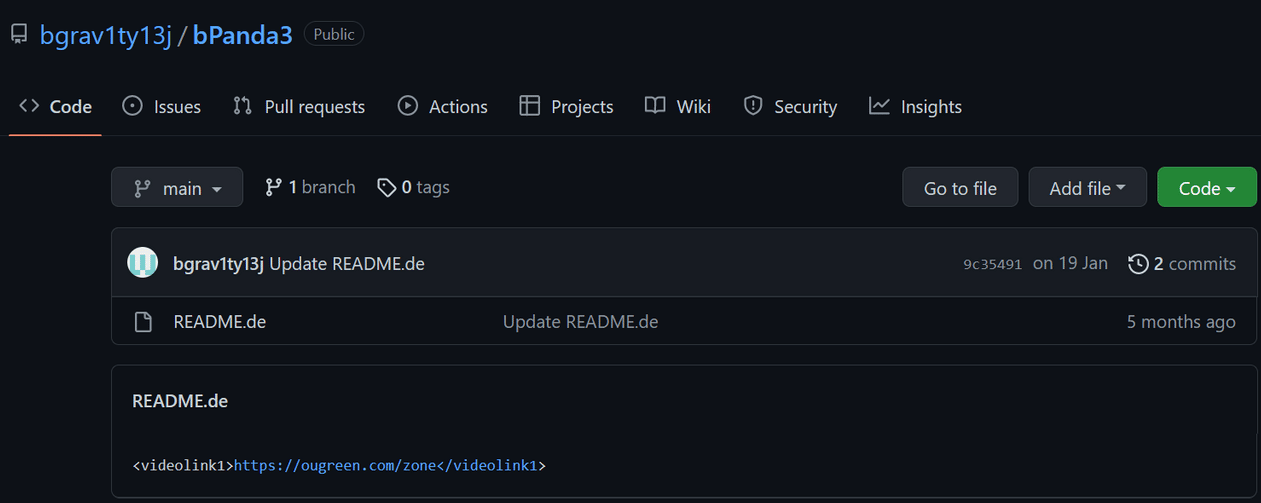
Finally, inside the GitHub pages, other endpoints can be obtained during the malware execution, probably the final C2 where data is sent, and the commands received.
Figure 5: vSingle — final C2 endpoint on GitHub repository
Learn Vulnerability Management
Final thoughts
Malware tactics, techniques and procedures are constantly changing. With this approach, Lazarus groups pretend to be away from the cybersecurity radar and extend their threats' life-cycle. Because GitHub is a legitimate source, identifying this kind of traffic as suspicious can be challenging.
Internet traffic should be limited to known sources if possible and monitored as well. Host-based security via EDR and AV systems should also be considered the key to identifying, blocking and tracking cyber threats early.
Sources:
- Lazarus operation, Infosec Institute
- VSingle analysis, JPCERT/CC
- Lazarus malware, JPCERT/CC