Whitespace obfuscation: PHP malware, web shells and steganography
Web shells are malicious entry-points used by crooks to interact with the server-side and execute commands remotely. In recent years, these kinds of web-based, shell-like interfaces have been improved and have become more stealthy, thus evading internal defenses and avoiding their detection.
This backdoor is specifically designed to provide subsequent access to a site or system. When the malicious code is executed on a target system, it can open the “doors” facilitating access to the attacker and allowing the bypass of the common authentication flow.
Learn Vulnerability Management
Although there are different kinds of web shells depending on the nature of the target system, we are going to analyze a PHP web shell that leverages the steganography technique to make it hard to detect and allowing the payload persistence for a long time.
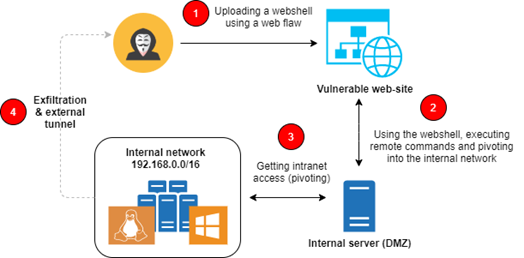
Figure 1: High-level diagram of a scenario using a web shell as an initial entry point.
As observed, criminals used known vulnerabilities to upload the malicious code into the remote web server to get code execution. After that, it’s possible to read and write on the server filesystem, upload and download files and also pivot into the internal network, opening the internal doors and then exposing the internal assets.
Steganography to hide the backdoor
A kind of PHP web shell was found by researchers from Sucuri Team in February 2021 that takes advantage of the usage of CSS files that revealed 56,964 seemingly empty lines containing combinations of invisible tabs (0x09), space (0x20) and line feed (0x0A) characters, which when converted to the binary representation are part of an executable JavaScript code.
Figure 2: Payload hidden in CSS files using steganography.
During the investigation, a file called license.php highlighted the researcher’s attention due to a strange block of code found during his analysis. In detail, the license text is placed inside a multi-line PHP comment. Nonetheless, on the 134 a gap between the comments with PHP code is visible.
Figure 3: PHP code along with blocks of comments.
This is not a new technique used by criminals to bypass detection. The PHP code is malicious, but its intent is not executing any kind of web shell payload or code execution.
Whitespace decoder
To understand how this piece of code works, we are going to isolate part of the code in a small piece as presented below.
Figure 4: PHP whitespace decoder.
In short, the code reads the file in chunks of eight chars and converts tabs (nine) and spaces (32) into ones and zeroes. After that, the output is then converted to a decimal number and a char using the chr() function. Using this approach, each octet of whitespaces is converted into a visible string. Finally, the function ‘base64_decode(str_rot13(gzdecode(…‘. is used to decode completely and execute the final payload.
Another way found on the initial code used by the PHP loader is a backup file created with a file name “ “ (just a space) and then executed. With this approach in place, the file name is less visible in file listings and evades detection. After execution, the file is deleted.
The license.php file contains the whitespaces (the final payload) at the end of the file - as presented in Figure 4.
Figure 5: Hex view of the last line of license.php file with the hidden payload.
After executing the script as previously explained, it was possible to reveal the final payload and essentially transform the whitespaces into executable PHP code, the PHP web shell.
Figure 6: Decoded web shell using steganography technique.
From this point, and with a bit of steganography, the web shell is executed on the server-side, and criminals can access the remote server, execute arbitrary commands, escalate privileges and so on.
Learn Vulnerability Management
Dealing with whitespace obfuscation
Obfuscation techniques are often used to hide code and make analysis and detection harder. There are dozens of popular kinds of obfuscations, and criminals are looking for new ways to avoid detection have persistent payloads. By using the steganography approach, criminals can hide the malicious code even under the human analysis as the malicious code is just a few lines of whitespaces when the target file is opened using a common text editor.
In this way, there is a set of activities that can be used to prevent these kinds of attacks:
- Prompt patching of webserver and plugin vulnerabilities
- Reduce the use of plug-ins (and third-party vulnerabilities)
- File integrity monitoring
- Malware scanning/endpoint protection software
- Network segmentation prevents lateral movement
- Server configuration review and hardening.
Sources:
webshell using steganography, Sucuri
zerologon and webshells, Segurança-Informática