Security Challenges in the Internet of Things (IoT)
The Global State of Information Security® Survey 2015 issued by PricewaterhouseCoopers comes to the conclusion that about 70% of connected IoT devices lack fundamental security safeguards. Prof. Scott Peppet is one of the proponents of the theory that IoT products are inherently vulnerable to security threats. Although there have not been any major incidents with respect to smart objects so far, risks are by all means more than theoretical. Just to name a few: Driverless cars have become legal in California since May 2014. In the meantime, stories like the Chrysler Jeep Hack and a $60 low-power laser that can affect driverless car performance by tampering with its sensors demonstrate flaws in the security of these autonomous vehicles. Not only cars, but drive-through car washes can be taken over via the Internet as well, a fact proved by Billy Rios, founder of Laconicly. Kaspersky's expert Roman Unuchek demonstrated security flaws in fitness bands (so-called wearables) at SAS 2015, which can be used by a potential attacker to connect a fitness band and retrieve information about the owner's location tracking. Even more dire consequences can happen when Internet-connected insulin pumps are compromised, and the same thing can be said for active pacemakers with wireless transmission inserted in patients' chests.
Learn IoT Security
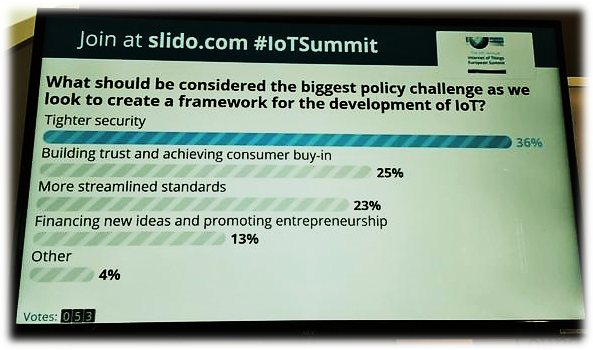
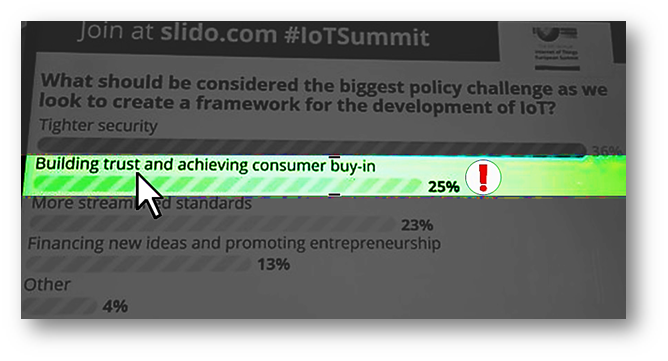
A survey made during the 6th Annual IoT European Summit in Brussels, Belgium
The main body of this article consists of two parts, titled "Common Security Characteristics of IoT Products" and "Specific Security Issues in IoT Products," whose role is self-explanatory. The third and final chapter—"Security as a Competitive Advantage"—goes on to suggest that the IoT market will probably smooth out irregularities in time, self-regulate, so to speak, including the security weaknesses that are common at the moment.
Common Security Characteristics of IoT Products
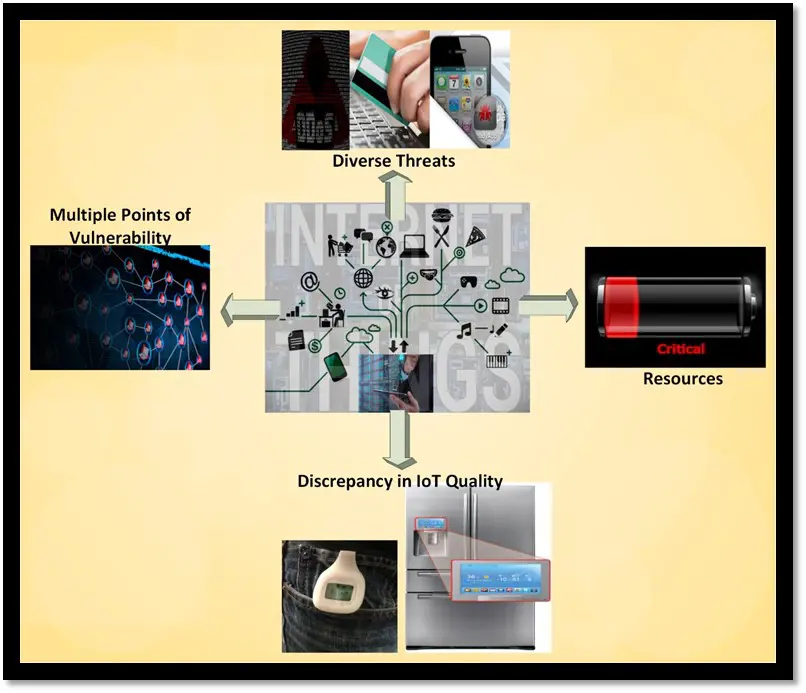
According to a great number of scholars, devices in the IoT world bring in a diverse array of potential security risks. Some of these risks are traditional threats for standard computers. For instance, new smart TVs that enable users to surf the Internet, purchase other "things," and share photos via social networks could put data stored or transmitted through the TV at risk. Sensitive bank card information, passwords, and personal data that can facilitate identity theft are some types of information attackers can get their hands on.
Speaking of wide-ranging threats, the IT security company Symantec discovered in November 2013 a new computer worm dubbed Linux.Darlloz that was engineered to target not only traditional computers, but also specific small IoT devices, such as smart TVs, web cameras, and home routers. After screening all the damages, it was concluded that wireless speaker systems and smart refrigerators were also hacked; just like a regular botnet composed primarily of traditional stationary computers, all of those devices enumerated above were used to send out malicious emails. More details on how it works:
The worm attempts to brute force access to those with well-known ID and password combinations. Should one of those work, it sends HTTP POST requests, which exploit the vulnerability. If the target is not running a patched version of PHP, it will download the worm from a malicious server and install it. That machine will then begin searching for its next target.
Evidently, compromised "things" can be surreptitiously harnessed to launch a massive distributed denial-of-service attack (DDoS) organized in a cluster of many computer devices, called a botnet, in order to perform in concert a concentrated cyber-attack. It is a known fact that, the more devices the malicious actor has under control, the more successful these DDoS attacks are; as connected sensor devices proliferate, security flaws will allow an attacker to take a large number of devices under his belt.
For that reason, installing more devices, connected to users (the so-called human-machine interaction), to other devices (machine-to-machine technology), or a combination thereof, will most likely increase the potential number of vulnerabilities an intruder could employ to compromise personal data. And predictions estimate that there will be 100 wi-fi chips on an average per home in the near future.
The concept of 'Multiple Points of Vulnerability' in the security of IoT system, in fact, includes the IoT product, embedded software, data inside the device, communication channels, data aggregation platform, and data centers for analysis of sensor data. Providing security for all of these surfaces is a serious challenge for businesses in this area. One senior executive explains that "[s]ecuring an IoT system involves securing the IoT product and implementing multiple features at the system level, such as access control and account management, segregation of networks and accounts, the use of secure protocols for data transmission, and the management of firewall and antivirus updates ." It is important to note that securing each IoT product is a key strategy to securing the IoT system in its entirety.
It is easier said than done. In reality, there is a great discrepancy in the quality of IoT devices as a whole, as some of them are sophisticated and expensive and others are cheap and disposable. Consumers may receive connected goods with powerful processors (e.g., Intel Atoms or ARMv8 chips), like smart washing machines and refrigerators, but these chips would be impractical for most IoT purposes, since the latter come with no display and limited battery capacity. Security vulnerabilities in one device may be used to facilitate attacks on other devices further down the line in a given consumer's network. Appropriating credentials from the weak device in order to break in to other more secure systems is the way to do it. In this context, the Target data breach is an extraordinary cyber-attack because hackers accessed the retailer's inner network through its Internet-connected air conditioners, heating and ventilation systems.
Security vs. efficiency is another dilemma of present-day IoT products. Manufacturers always try to balance out one of the most critical factors when it comes to resource constraints—battery deficiency—and device security. It is not clear at the moment what is the correct solution to implementing the confidentiality, integrity, and availability measures without impacting negatively the optimization of energy or/and computational resources .
As was explained before, apparatuses used in the IoT are not easy to be made secure, both for business and technical reasons. They are vulnerable to physical or cyber-attacks (e.g., eavesdropping or proxy attacks) because they usually rely on wireless communication infrastructure, which is often entirely unprotected, and they have a very limited amount of battery and computing power. Public key infrastructure (PKI) is a widely-used method for securely exchanging data over networks, but it does not seem to work well with IoT devices, given their weak computing capabilities to cope with processing tasks.
What is specific for the IoT conveyor belt assembly line is that there is a complex supply chain with many entities taking on various degrees of responsibility. A security breach may occur at any entry point, especially when taking into account the specific exchange of data among devices in a typical M2M setting. Perhaps lightweight protocols could be established to work on a mission to alleviate the chronic low resource syndrome in IoT devices.
Specific Security Issues in IoT Products
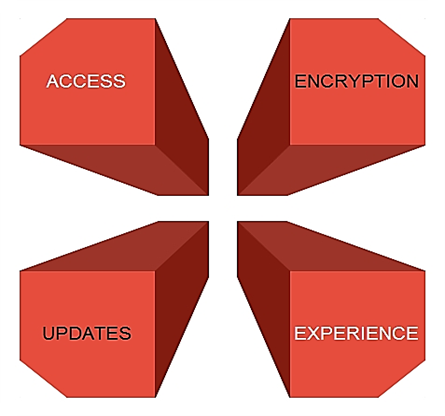
Unauthorized Access
One of the most challenging security problems with smart devices is resiliency against exposure to physical attacks. IoT objects are often left unattended and therefore are easy prey for a malicious actor who can capture them and then extract cryptography secrets, meddle with or modify their programming, or replace these devices with pre-exploited ones under his control. Devices manually built to capture user login information at the source level give cause for concern. An example of such a device is seemingly innocuous USB wall chargers that crack Microsoft wireless keyboard and then send the data wirelessly to the attacker's device.
Unauthorized access could result in creating perceptible risks to physical safety, but IoT can be accessed from afar as well. There are reports showing that insulin pumps can be hacked remotely to deliver deadly doses of the medicine in question or skip scheduled injections. Moreover, a series of experiments has proven that a car's internal computer network can be accessed through a built-in telematics unit without even physically touching the car. In the most recent case belonging to this type of unauthorized access attacks against IoT products, Axelle Apvrille, a security researcher working for Fortinet, gave a presentation at the Hack Lu 2015 conference on how Fitbit Flex can be hacked via its Bluetooth radio. Within Bluetooth range, i.e., 15 feet, she needed access to the device for just about 10 seconds. Once the compromise was done, Apvrille was able to manipulate the data in Fitbit Flex and even deliver code to a computer connected to the device for data synchronization.
As one HP study proves by revealing 250 security defects in ten commonly utilized IoT appliances—such as web cameras, TVs, home alarms, door locks, and thermostats—security features embedded in IoT devices are not good enough. Some of them have weaker factory-made authentication features that immediately expose them to security threats. In fact, either 8 out of 10 of these "things" failed to set up stronger password authentication than "1234" or the password given by the manufacturer by default is never changed at all. Passwords are the lowest hanging fruit when it comes to authentication, and many IoT devices rely on it. Most of the IoT devices, moreover, have a limited user interface, with no keyboards or screens, which in turn makes the implementation of password authentication system weak by default. That is why smart appliances can be susceptible to brute-force or dictionary attacks.
In a world where everything is connected to everything, and not always in the sense of technology, access to data about energy consumption collected by an energy-smart meter can give away whether the homeowners are absent from home (the "inference" problem).
Encryption
Let's have a look at three cases that will help us identify the problem in question:
"In 2014, an Israeli security firm uncovered a critical vulnerability in a telematics device developed by Zubie – a U.S.-based connected-car startup. The research team found that Zubie's hardware, which tracks a car's performance to provide drivers with instructions on improving driving efficiency, did not encrypt communications between the device and server. Researchers were able to demonstrate how hackers could exploit this weakness to send malicious updates to the device, steal data on the car's location and performance, and even unlock doors remotely."
An excerpt from
Securing the Internet of Things Opportunity: Putting Cybersecurity at the Heart of the IoT
by Capgemini Consulting
Another study of nine video baby monitors, conducted by Rapid7 senior security consultant Mark Stanislav, identified several common security issues and ten new vulnerabilities: a lack of encryption for communications and data storage, the availability of a command-line interface on a network port and backdoor accounts with weak passwords, backdoor credentials, cross-site scripting, authentication bypass, and privilege escalation. This case displays how more than one of the security issues examined in this article can be found to exist simultaneously in a single device. Stanislav further explains that "the findings do not apply only to video baby monitors, but provide a good sense of what consumer IoT security looks like in general."
The final illustration is about a couple of researchers from Florida International University who proved in 2013 that the Fitbit fitness tracker was vulnerable to various security attacks, and even unsophisticated toolkits could eventually capture data from any such fitness device within 15 feet, simply because the device was not created with security in mind (it used plain HTTP in its communications).
Perhaps, after these vivid examples, everyone will as themselves the question: What lies at the heart of the problem? In short, because of the small size, low power and computational incapacity of such devices, it is difficult to add security measures like encryption. The U.S. Federal Trade Commission (FTC) chairwoman, Edith Ramirez, who addressed the Consumer Electronics Show in Las Vegas earlier this year, likewise confirmed that "the small size and limited processing power of many connected devices could inhibit encryption and other robust security measures."
These examples and others make it evident that IoT devices have specific operational constraints and implementing any security measures should take them into account. Processing power is needed to support more secure measures for data transmission, such as encryption. To explain this point, The Article 29 Data Protection Working Party, a prominent advisory organization in the EU (henceforth "the Working Party"), announced that most sensors today "are not capable of establishing an encrypted link because of the priority given to the physical autonomy of the device or to cost control."
But will this incapability serve as an excuse for companies processing personal data in the context of IoT to provide loose security? It is highly unlikely that consumers will condone compromises on their safety. As the FTC's "Internet of Things: Privacy & Security in a Connected World" states, "companies must take additional steps to encrypt [the information] or otherwise secure it." It means that alternative methods for safely data processing should be introduced.
Therefore, where reduced resources capacity may expose to risk the communication between connected devices, it is even more necessary than ever data controllers, inter alia, to comply with the principle of data minimization and limit the processing of personal data, particularly the data stored on these devices, to the absolute minimum required.
Plus, machines are not always configured by the user if they are designed to be directly accessible through the Internet. Running with default settings can give a convenient access point to cyber-villains. Hence, restricting network access, disabling by default non-essential functionalities, and non-use of untrusted software and update sources will contribute to narrowing down the attacking surface open for data breaches. Protective measures like those should be built in right from the outset, thereby directly applying the "Privacy by Design" principle.
Updates & Patches
Connected devices need to be updated on a regular basis in order to remain immune at least to extremely unsophisticated cyber-threats. The risk of cyber-attacks increases if patches are not updated frequently. In spite of this fact, it is shown that no more than 49% of companies offer remote updates for their smart "things."
There are more than one or two reasons for this. An underlying problem is that firms, especially those involved in the development of low-end devices, may lack economic incentives to give continuous support, which will leave the consumers shortly after the purchase with an unsupported IoT unit that may contain numerous security defects. Most IoT products are built from inexpensive chips and other materials, a fact which in itself does not incentivize manufacturers to provide security patches for them.
On the other hand, the reason could be that IoT vendors may not have the technical expertise to develop such updates. In some instances, the underlying issues is the lack of communication channels for the company to remotely deliver the patches, because it is more convenient for these companies (41%) to let consumers download and install them manually. Seen from the consumers' point of view, however, this may not work well for them because some of them experience difficulties installing the updates, or may not be at all aware (67%) of their existence in the first place. There are cases in which a security vulnerability is found ex-post production and it may be not so easy for data controllers to provide an update or apply a patch to it; and even if these remedies do exist, the majority of consumers may never find out about them.
Another weakness in the presence of unpatched vulnerabilities is that they can be indexed by specialized search engines. Even when customers are familiar with the existence of vulnerabilities, they may not be able to access the vendor's updates due to hardware limitations or technologies that are out of date and prevent the device from providing support to software updates. Consumers must be informed in cases when their devices are likely to be exposed to dangers because of existing unfixed flaws. Yet, should an IoT manufacturer cease to maintain a given device, alternative methods to provide support need to be introduced on short notice. It should be noted also that compromise of vendor's update server may negatively affect all of the devices at once. That is why firmware update mechanisms should not be automated on every device.
Lack of Experience
To begin with, IoT devices are often engineered by consumer goods manufacturers, not PC hardware or software businesses. Unfortunately, some of the developers approaching the market of networked devices, unlike hardware and software firms, lack the experience of having properly secured products and services from wrongdoers.
On the other hand, the potential risks referred to in the last paragraph illustrate how securing IoT devices may be more difficult than securing conventional stationary computers. Designing secure IoT products requires a bundle of multiple skills that would consider the app, device, and entire infrastructure, without leaving out the communication channel. The shortage of experienced security experts specializing in IoT tech trends is the main obstacle to creating secure environment for all those elements enumerated above, according to 35% of the respondents in a study.
New entries may not have the experience to cope with security problems in IoT, but it is also possible that experienced IoT manufacturers may find it hard to keep up with the rapid tempo of the new digital revolution. As a result, securing data may not be a priority item on the agenda of current IoT manufacturers.
While users of IoT devices generally care about security, they do not bother with it at all. For them, a connected refrigerator is still a refrigerator. Consumers guided by aggressive marketing campaigns rarely tend to see the connectivity option as something that can influence the physical world. Chucky is the famous movie doll possessed by the soul of a serial killer, and now this fictional story may come to life with the technical progress that brings into being toys like smart Barbies. No matter how secure these apparatuses are, companies should actively educate users on how to use them safely, through instruction either available online or on the packing.
Of course, such a policy of openness should not be implemented at the expense of training technical support staff. Perhaps a small group of employees working for the company should be trained to be able to teach costumers how to apply the best security practices—how to change passwords on a regular basis and manage access control the right way, for instance—and even resolving low-key security problems on their own.
And, last but not least, IoT developers need not only focus on security threats originating from outside like external hacking, but they also need to attend to employees and vendors-specific practices.
Conclusion: Security as a Competitive Advantage
Although there is an ever-growing tendency of cyber-attacks targeting IoT devices, based predominantly on plenty of warnings from distinguished security experts, most of the companies nowadays do not envisage adequate privacy and security safeguards for their Internet-enabled sensor products. Only 33% of surveyed executives express firm belief that their products are resilient enough to withstand persistent cyber-threats.
Reportedly, medical device manufacturers and home automation are among the most endangered industry segments, as far as cybersecurity is concerned. It is really worrying, given the anticipated sky-high demand for IoT products in these sectors—the expected growth is estimated to reach the astounding figure of over 19 million patients by 2018. A survey by Capgemini Consulting shows that 71% of consumers' choices for purchasing IoT products will be affected by security concerns. Firms in some areas, for example, industrial manufacturing and smart metering, will be affected to a greater extent than other segments like home automation and automobiles.
Without a doubt, IoT corporations that demonstrate readiness to comply with privacy, data protection and ethical practices will win costumer trust and gain competitive advantage in this brand-new connected world. BlackBerry's marketing strategy, for instance, aims at leveraging its network and mobile data security supremacy to become a leader in the market of the Internet of Things. What is new and different than the strategies of its competitors is that the IoT platform will enable its customers to build up secure IoT applications. This platform will further contain far-reaching wi-fi software updates. BlackBerry intends to target its marketing first at automotive and shipping sectors, and then to gradually extend its influence to other global industry verticals, such as energy and healthcare. Project Ion is an initiative organized by BlackBerry that will lay the foundation for an efficient and secure IoT platform. It will be based on a secure platform for data collection from across a diverse range of devices and environments, as well as establishing a proactive policy for building lasting strategic partnerships between business partners, carries and application developers.
So a falling economy forces companies to innovate in every imaginable way so as to remain competitive. For many companies, this means to connect their "thing" to the Internet, just because this is the current market trend or fashion. IoT products are becoming more and more ubiquitous since this shift in technology clearly has the potential to develop the business ecosystem, globally speaking, and, at the same time, to improve the quality of life of the average consumer.
However, users of smart "things" seem to value companies that care about the security of their clients. As the ISACA's Internet of Things research shows, 89% of the users consider it important that a data security professional entrusted with access to their users' personal information possesses a cybersecurity certification. Consequently, security is an important matter to everyone and, in the race between fast innovation and managing risk, those who wish to succeed will have to learn to juggle both. People were also frightened when the car was introduced to them for a first time, but they have come to appreciate the benefits of the invention, as they will appreciate the benefits given to them by the IoT.
Reference List
AFCEA (2015). The security implications of the Internet of Things. Available at http://www.afcea.org/mission/intel/documents/InternetofThingsFINAL.pdf (17/11/2015)
Barcena, M., Wueest, C. & Lau, H. (2014). How safe is your quantified self? Available at http://www.symantec.com/content/en/us/enterprise/media/security_response/whitepapers/how-safe-is-your-quantified-self.pdf (17/11/2015)
Capgemini Consulting (2014). Securing the Internet of Things Opportunity: Putting Cybersecurity at the Heart of the IoT. Available on http://www.capgemini-consulting.com/resource-file-access/resource/pdf/securing_the_internet_of_things.pdf (17/11/2015)
Drozhzhin, A. (2015). Internet of Crappy Things. Available at https://blog.kaspersky.com/internet-of-crappy-things/7667/(17/11/2015)
Finch, B., Polidora, R., Meyer, C., Lutz, L. & Shecter, P. (2015). How to Fail in the Internet of Things. Available on http://www.pillsburylaw.com/siteFiles/Publications/AlertFeb2015PrivacyHowtoFailintheInternetofThings.pdf (17/11/2015)
Fink E. & Segall L. (2013). Your TV might be watching you. Available at http://money.cnn.com/2013/08/01/technology/security/tv-hack/ (17/11/2015)
FTC (2015). Internet of Things Privacy & Security in a Connected World. Available on http://www.ftc.gov/system/files/documents/reports/federal-trade-commission-staff-report-november-2013-workshop-entitled-internet-things-privacy/150127iotrpt.pdf (17/11/2015)
Hayashi, K. (2013). Linux Worm Targeting Hidden Devices. Available at http://www.symantec.com/connect/blogs/linux-worm-targeting-hidden-devices (17/11/2015)
Hajdarbegovic, N. (2015). Are We Creating An Insecure Internet of Things (IoT)? Security Challenges and Concerns. Available at http://www.toptal.com/it/are-we-creating-an-insecure-internet-of-things (17/11/2015)
HP.com (2014). HP Study Reveals 70 Percent of Internet of Things Devices Vulnerable to Attack. Available at http://www8.hp.com/be/nl/hp-news/press-release.html?id=1744676 (17/11/2015)
Hu, E. (2014). What Do You Do If Your Refrigerator Begins Sending Malicious Emails? Available at http://www.npr.org/blogs/alltechconsidered/2014/01/16/263111193/refrigerator-hacked-reveals-internet-of-things-security-gaps (17/11/2015)
Kirk, J. (2012). Pacemaker hack can deliver deadly 830-volt jolt. Available at http://www.computerworld.com/article/2492453/malware-vulnerabilities/pacemaker-hack-can-deliver-deadly-830-volt-jolt.html (17/11/2015)
Kolochenko, I. (2015). How to secure connected devices before it will be too late? Available at http://www.csoonline.com/article/2983681/vulnerabilities/how-to-secure-the-internet-of-things-and-who-should-be-liable-for-it.html (17/11/2015)
O'Brien, D. (2014). The Internet of Things: New Threats Emerge in a Connected World, SYMANTEC. Available at www.symantec.com/connect/blogs/internet-things-new-threats-emerge-connected-world (17/11/2015)
Olswang-Escribano, B. (2014). Privacy and security in the Internet of Things: challenge or opportunity. Available on http://www.olswang.com/media/48315339/privacy_and_security_in_the_iot.pdf (17/11/2015)
Peppet, S. (2014). Regulating the Internet of Things: First Steps Toward Managing Discrimination, Privacy, Security, and Consent. Available on http://www.texaslrev.com/wp-content/uploads/Peppet-93-1.pdf (17/11/2015)
Potoczny-Jones, I. (2015). IoT Security & Privacy: Reducing Vulnerabilities. Available at http://www.networkcomputing.com/cloud-infrastructure/iot-security-and-privacy-reducing-vulnerabilities/a/d-id/1322921 (17/11/2015)
Radcliff, J. (2011). Hacking Medical Devices for Fun and Insulin: Breaking the Human SCADA System. Available at https://media.blackhat.com/bh-us-11/Radcliffe/BH_US_11_Radcliffe_Hacking_Medical_Devices_WP.pdf (17/11/2015)
Rahman, M., Carbunar, B., Banik M. (2013). Fit and Vulnerable: Attacks and Defenses for a Health Monitoring Device. Available at http://arxiv.org/pdf/1304.5672v1.pdf?goback=.gde_2206357_member_236224214 (17/11/2015)
Schneier, B. (2014). The Internet of Things Is Wildly Insecure—And Often Unpatchable. Available at https://www.schneier.com/essays/archives/2014/01/the_internet_of_thin.html (17/11/2015)
Shepardson, D. (2015). Report: Cars are vulnerable to wireless hacking. Available at http://www.detroitnews.com/story/business/autos/2015/02/08/report-cars-vulnerable-wireless-hacking/23094215/ (17/11/2015)
The Article 29 Working Party. Opinion 8/2014 on the on Recent Developments on the Internet of Things (WP223). Available on http://ec.europa.eu/justice/data-protection/article-29/documentation/opinion-recommendation/files/2014/wp223_en.pdf (17/11/2015)
Learn IoT Security
Wired.com (2014). The Internet of Things Is Wildly Insecure — And Often Unpatchable. Available at http://www.wired.com/2014/01/theres-no-good-way-to-patch-the-internet-of-things-and-thats-a-huge-problem/ (17/11/2015)









